JWT decoder
/Your data is 100% private -- JWT is fully decoded and encoded directly on your device.
Learn about JWT
All information you concern about JWT and step-by-step guide to verify JWT in diverse framework.
What is JWT?
JWT (JSON Web Token) is a self-contained, stateless token that carries information in a structured and readable format. Whether you’re protecting an API or adopting token-based authentication for your application, JWTs are a powerful tool, because they:
- Stateless: JWTs are self-contained and do not require server-side state to validate. JWT can ensure data integrity via signatures.
- Cross-service compatibility: JWTs can be easily shared and verified across different services.
- Extensible: The payload of a JWT can contain custom claims, allowing for flexible authorization and info sharing.
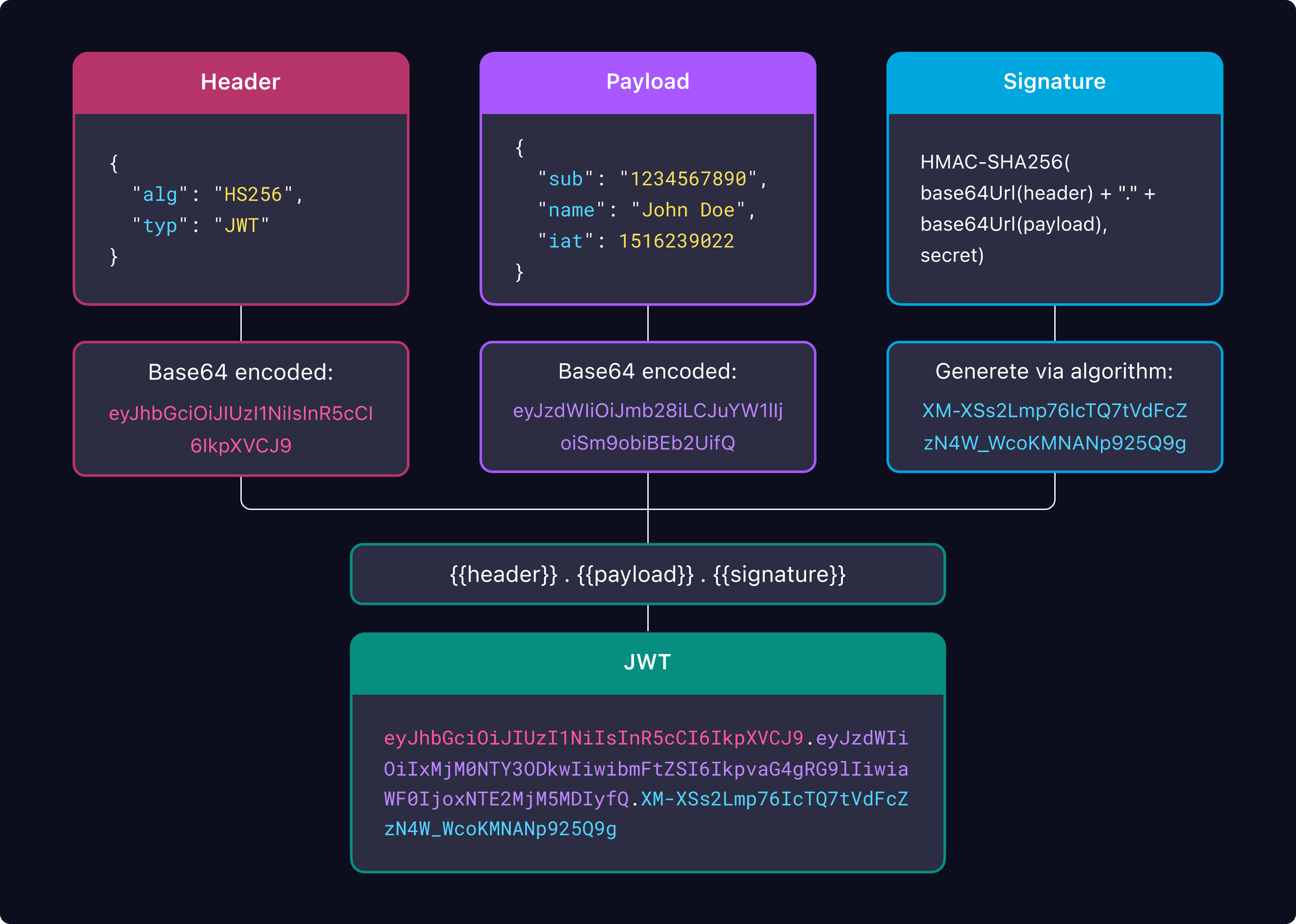
The structure of JWT
A typical JWT is split into three parts, each encoded in Base64URL and separated by periods (.):
- Header - Contains metadata, such as the signing algorithm (e.g., HS256 or RS256) and the token’s type (JWT).
- Payload - Contains the actual data, like user ID, user profile, expiration time, or scopes.
- Signature - A hashed combination of the Header, Payload, and secured using a secret key. Its purpose is to ensure the token's integrity and confirm that it has not been altered
This structure enables JWTs to provide a compact, secure way of transmitting information between parties.
Common token claims in JWT
The claims are part of the payload and hold the key information. Here are standardized Registered Claims for your refer:
| Claims | Full name | Description |
|---|---|---|
| iss | Issuer | The entity that issued the JWT, like the authorization server. |
| sub | Subject | Identifies the JWT's subject, typically representing the authenticated user. |
| aud | Audience | Specifies which recipients can accept and process the token. This can be an array of values for multiple audiences or a single value for a single recipient. |
| exp | Expiration Time | Sets an expiration time on the token after which it becomes invalid. This helps prevent replay attacks by limiting how long a token remains valid. |
| nbf | Not Before | Makes a token valid only after this timestamp. Helpful in situations where clocks are not accessible. |
| iat | Issued At | When the token was created. This can be used to determine the token's age. |
| jti | JWT ID | A unique identifier for the token, useful to prevent the same token from being used multiple times (e.g., in replay attacks). |
Depending on the specification and the configuration of the authorization server, additional claims may be included in the payload to support specific use cases. You can also add custom claims to JWT to meet unique business requirements.
ID Token
Used in OpenID Connect, it includes claims like profile information (e.g., name, email, etc.) about the authenticated user.
Access Token
Used in OAuth 2.0, it grants access to specific resources or APIs on behalf of the user or application.
When to use JWT?
JWTs can be particularly beneficial in the following scenarios:
- Microservices architecture: For stateless authentication across multiple services.
- Single sign-on (SSO) systems: Enabling access to multiple applications with one authentication.
- Mobile applications: Efficiently maintaining user sessions across API calls.
- High-traffic applications: Reducing database load in high-volume environments.
- Cross-origin resource sharing (CORS): Simplifying authentication across multiple domains.
- Serverless architectures: Providing stateless authentication where server-side sessions are challenging.
How to verify JWT?
The integrity of a JWT must be verified to ensure its header and payload have not been tampered with. Below are step-by-step examples for verifying JWTs in popular programming environments:
- Verify JWT in RubyGrape / Ruby on Rails / Sinatra
- Verify JWT in .NETASP.NET Core
- Verify JWT in JavaMicronaut / Quarkus / Spring Boot / Vert.x Web
- Verify JWT in PHPLaravel / Lumen / Symfony
- Verify JWT in PythonDjango / Django REST / FastAPI / Flask
- Verify JWT in GoChi / Echo / Fiber / Gin
- Verify JWT in Node.jsExpress / Fastify / Hapi / Koa / NestJS
- Verify JWT in RustActix Web / Axum / Rocket
Related JWT topics
All information you concern about JWT and step-by-step guide to verify JWT in diverse framework.
- JWT algorithms: EC vs. RSADive into the signature algorithms of JWT, such as EC and RSA, and learn how to choose the most secure and efficient method for your application.
- ID token & Access token & Refresh tokenDo you know the specific purposes of ID Tokens, Access Tokens, and Refresh tokens? Understand their roles in authentication and authorization processes from a JWT perspective.
- Custom JWT token claimsHow does JWT achieve fine-grained access control? Compare RBAC (Role-Based Access Control) and ABAC (Attribute-Based Access Control) to find the best solution for your application.
- Opaque token vs. JWT tokenExplore the core differences between JWT and Opaque Tokens, and discover why JWT has become the modern choice for authentication with its high performance and scalability.
- API authorization: API keys vs. Basic authentication vs. OAuth JWT tokensExplore three common API authorization mechanisms with their pros and cons. Dive into a best practice about for safeguarding your APIs using OAuth JWT tokens.
- JWT vs. Session authenticationSession-based auth relies on server-side storage to maintain user sessions, whereas token-based auth enables stateless and scalable communication between clients and servers. Discover how JWT is revolutionizing API security and why it’s becoming the preferred choice for modern authentication.
- OAuth 2.0 & OIDC & SAMLThe fancy terms like OAuth, OpenID Connect (OIDC), SAML, SSO, and JWT are frequently used in the domain of identity and access management (IAM), but what do they mean? How do they work together?
Unlock more with Logto Cloud
Simplify your workflow and ensure secure user management with Logto Cloud. Built on OpenID Connect (OIDC), it leverages JWT to deliver a reliable authentication and authorization system designed to scale with your needs.