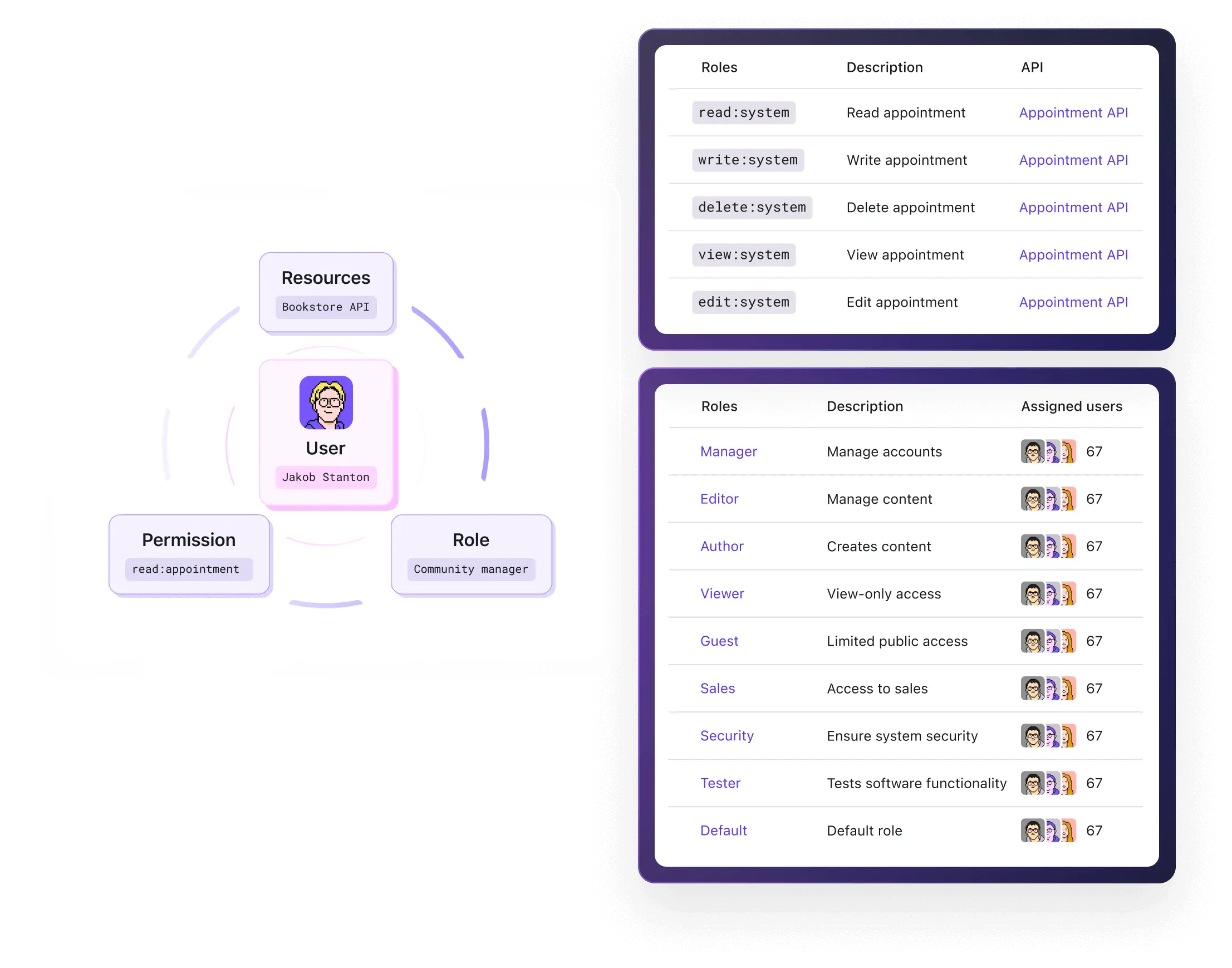
RBAC plays a critical role in achieving business maturity
Role-Based Access Control (RBAC) helps reduce data breaches and security by limiting access to sensitive information and systems based on user roles.
Principle of least privilege
Users are granted only the permissions they need to perform their specific job functions.This minimizes the risk of accidental or intentional misuse of data by restricting unnecessary access.
Simplified access management
Permissions are assigned to roles, not individual users, making it easier to manage and audit access. This reduces errors in granting or revoking access, ensuring consistent enforcement of security policies.
Widely used mechanism in authorization
Many regulations (e.g., GDPR, HIPAA) require strict access control. RBAC ensures compliance by enforcing structured, role-based access policies. This avoids fines and reputational damage due to non-compliance.
Take control of access management
Logto offers a range of RBAC features that simplify access control management without causing mental exhaustion
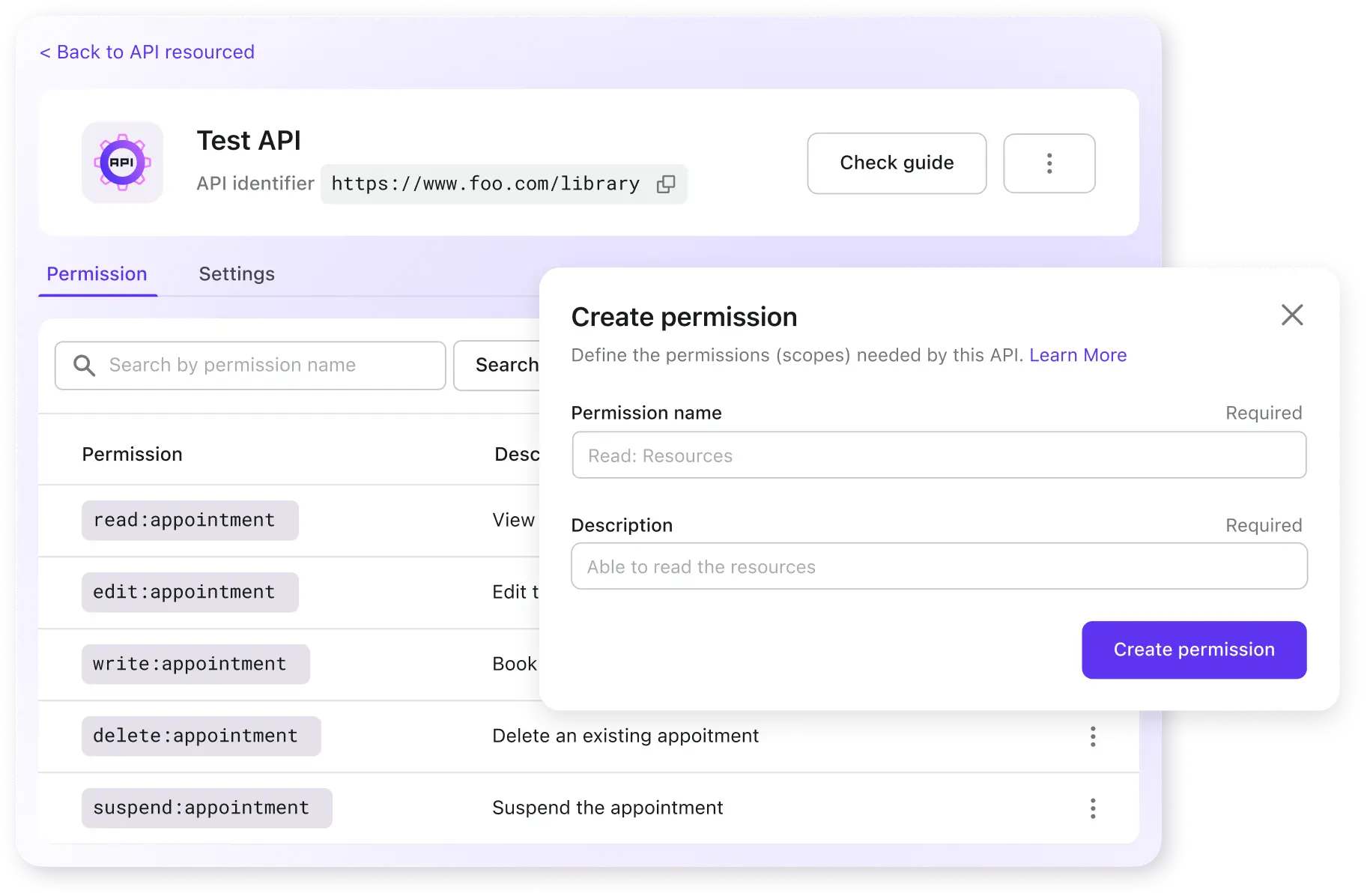
Protect your API
By adding permissions to your API resources and incorporating them into your development process, you can exercise granular control over the authorization of the API resource within a minimized scope.
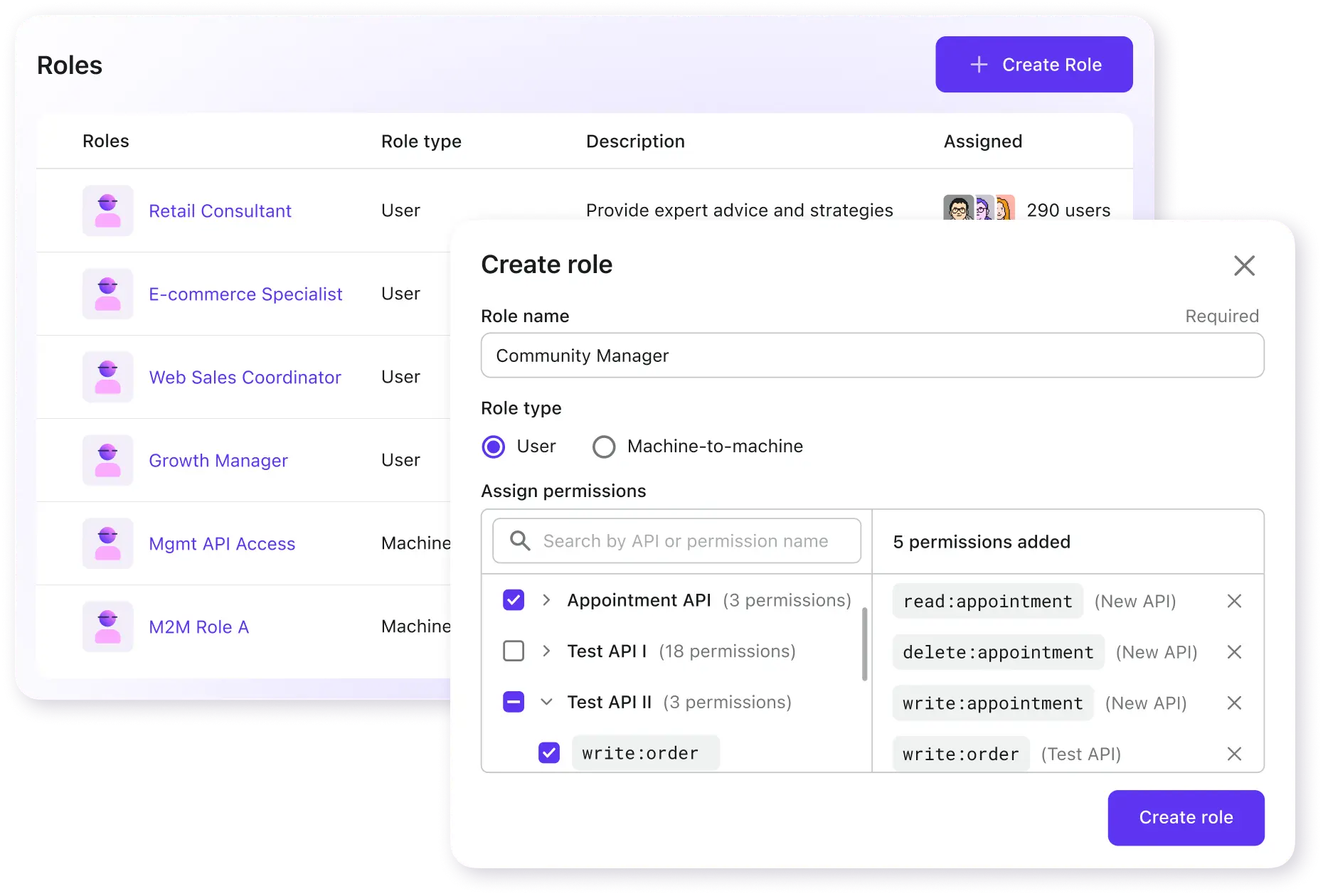
Using roles for efficiency and effectiveness
Directly mapping permissions to users is inefficient, which is where roles come in. With RBAC, roles include permissions, and you can efficiently manage access in batches.
- Global roles: Assigned across the Logto tenant
- Organization roles: Assigned within an org
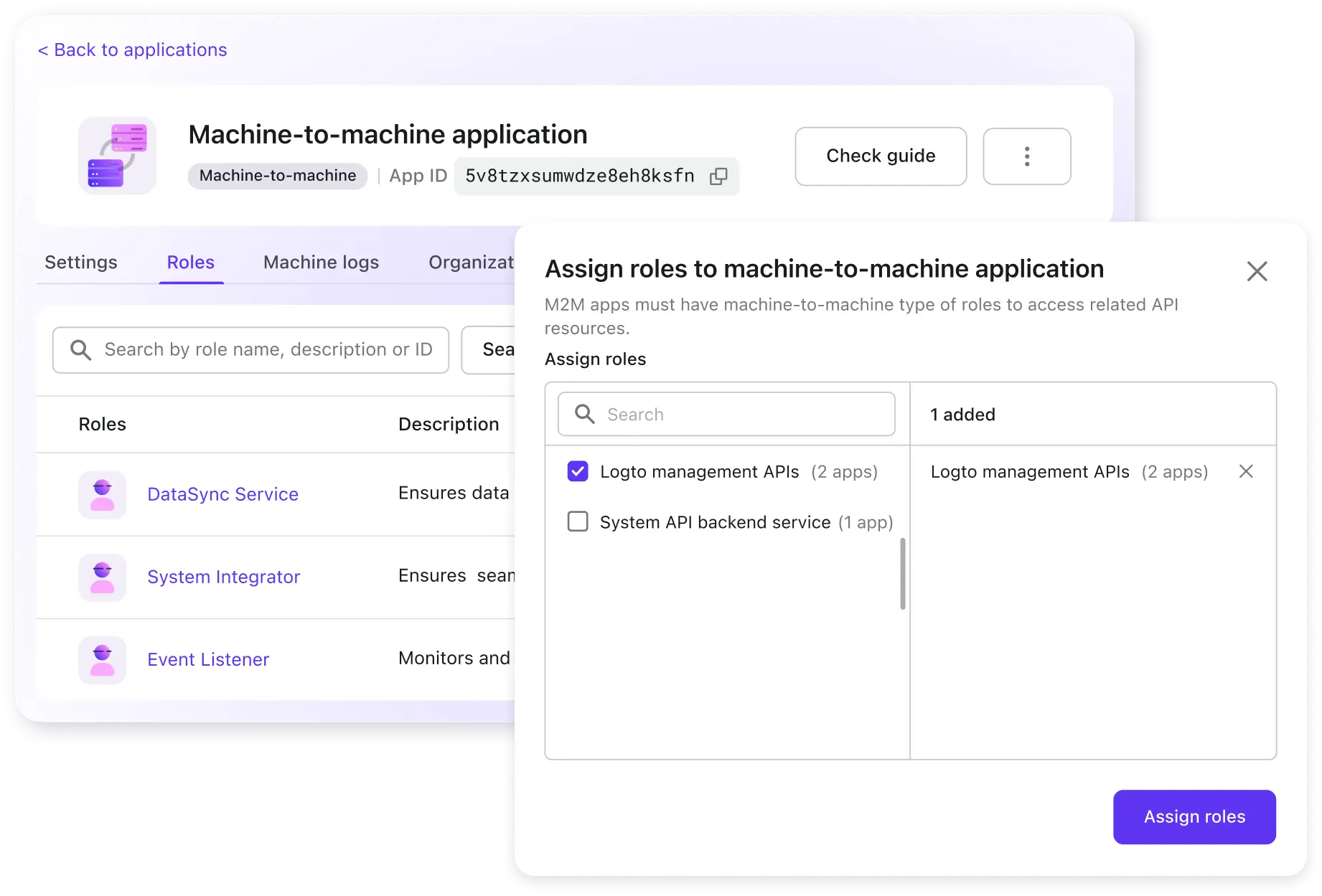
Use RBAC to protect your M2M authentication
Roles can also be assigned to machine-to-machine application, this can protect your API authentication and server to server communication.
From authentication to authorization, Logto has you covered
Don't settle for authentication-only solutions. Our RBAC authorization system offers thorough authorization features, setting us apart from the competition.
Best developer experience
- From code to no code with smooth workflows
- Easy to migrate from Auth0
- Adhering to the NIST RBAC model
Extensive authorization service support
- Highly effective role-based access control features
- Detailed tutorial ready
- Allowing for a wide range of scenarios
Frequently asked questions
Can Logto be used for attribute-based access control (ABAC)?
Is RBAC feature available by default?
Does Logto support multiple role assignments?
Unlock more with Logto Cloud
Gain greater control over access permissions and improve security with Logto's powerful RBAC (role-based access control)