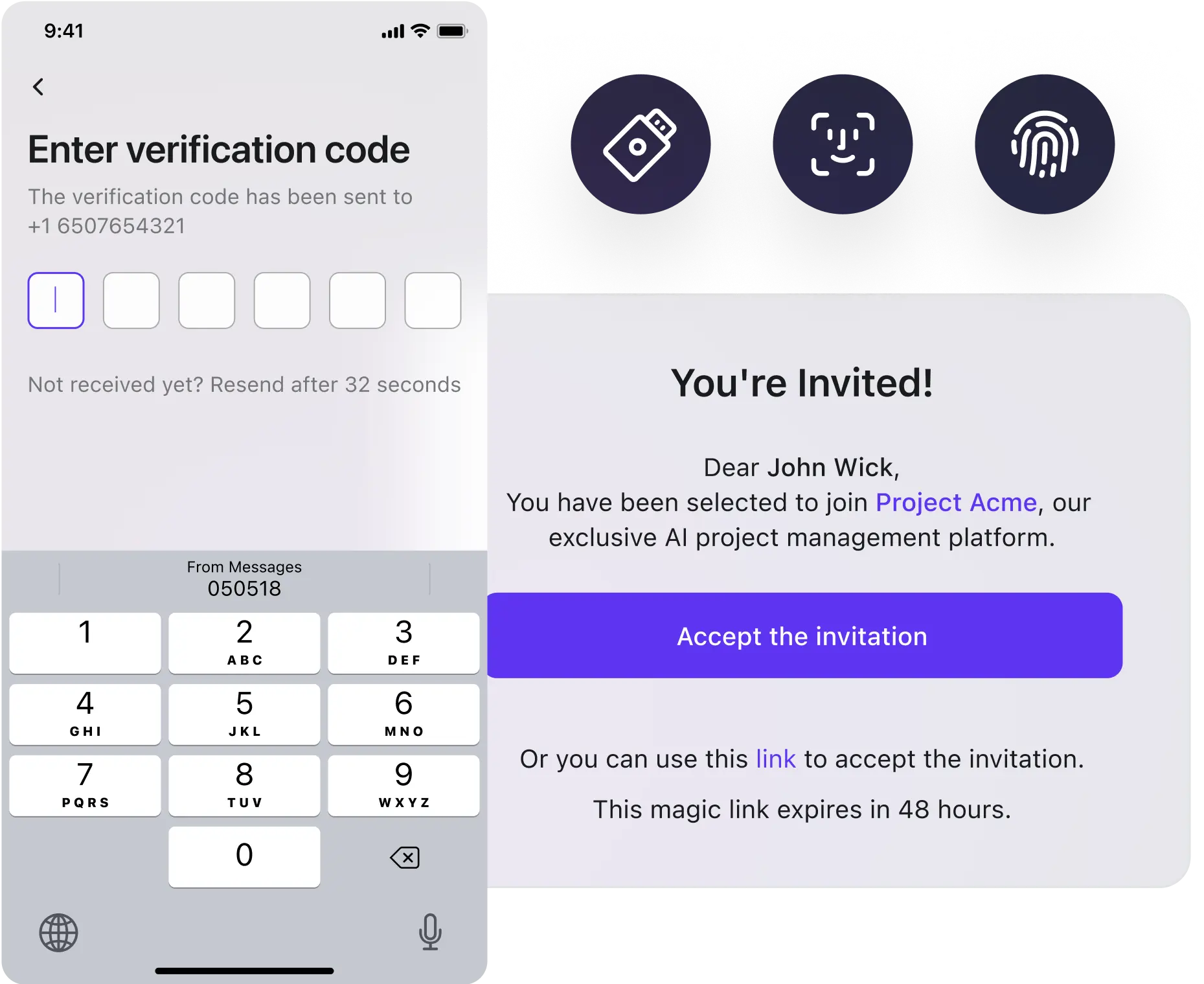
How does Logto passwordless work
Email and verification code is a secure, user-friendly method that eliminate the need to remember passwords. Here is how the user flow for this process typically unfolds:
Step 1: User enter email or phone number
The journey begins when a user lands on the sign-in/up page. Here, they are prompted to enter their email address.
Step 2: Code generation and delivery
Once the email is submitted, the system generates a unique code. This verification code is then sent straight to the user inbox.
Step 3: Code entered, access granted
Upon enter the code to the interface, the application receives the access token. This token serves as proof of identity and is used to authenticate the user without requiring a password.
Logto key features to cover your requirements
Passwordless comes with several touchpoints throughout the user journey. If you build your own, you need to prepare for things like email service, email design, and MFA—but Logto has those covered.
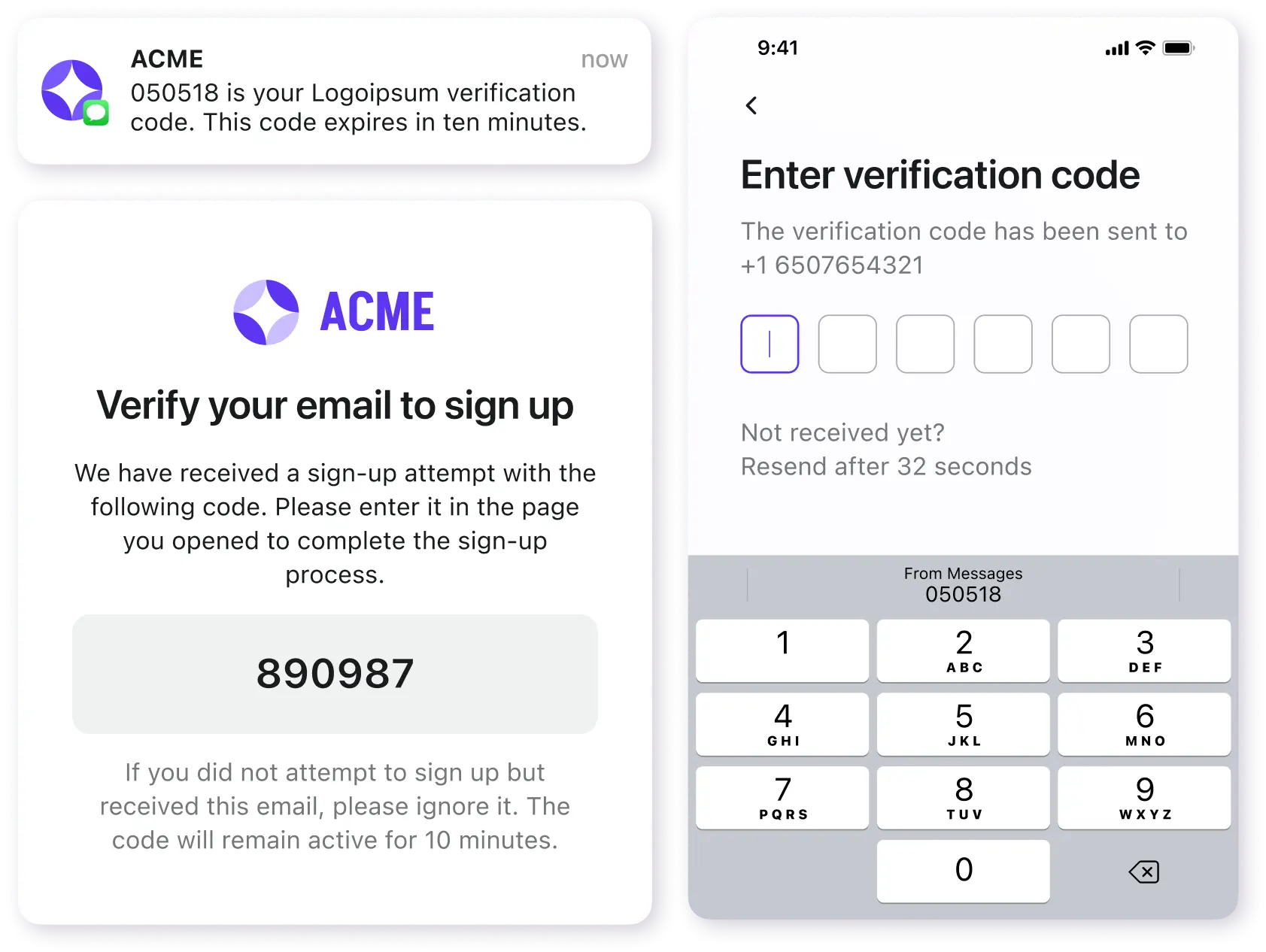
Email / SMS OTP
Deploy ready-made, easily tailored email and SMS verification flows for every customer touchpoint. No matter the device.
- Support cross device experience
- Sign-in, sign-up, password recovery
- Step-up verification, account linking and updating
- Customizable email / SMS templates
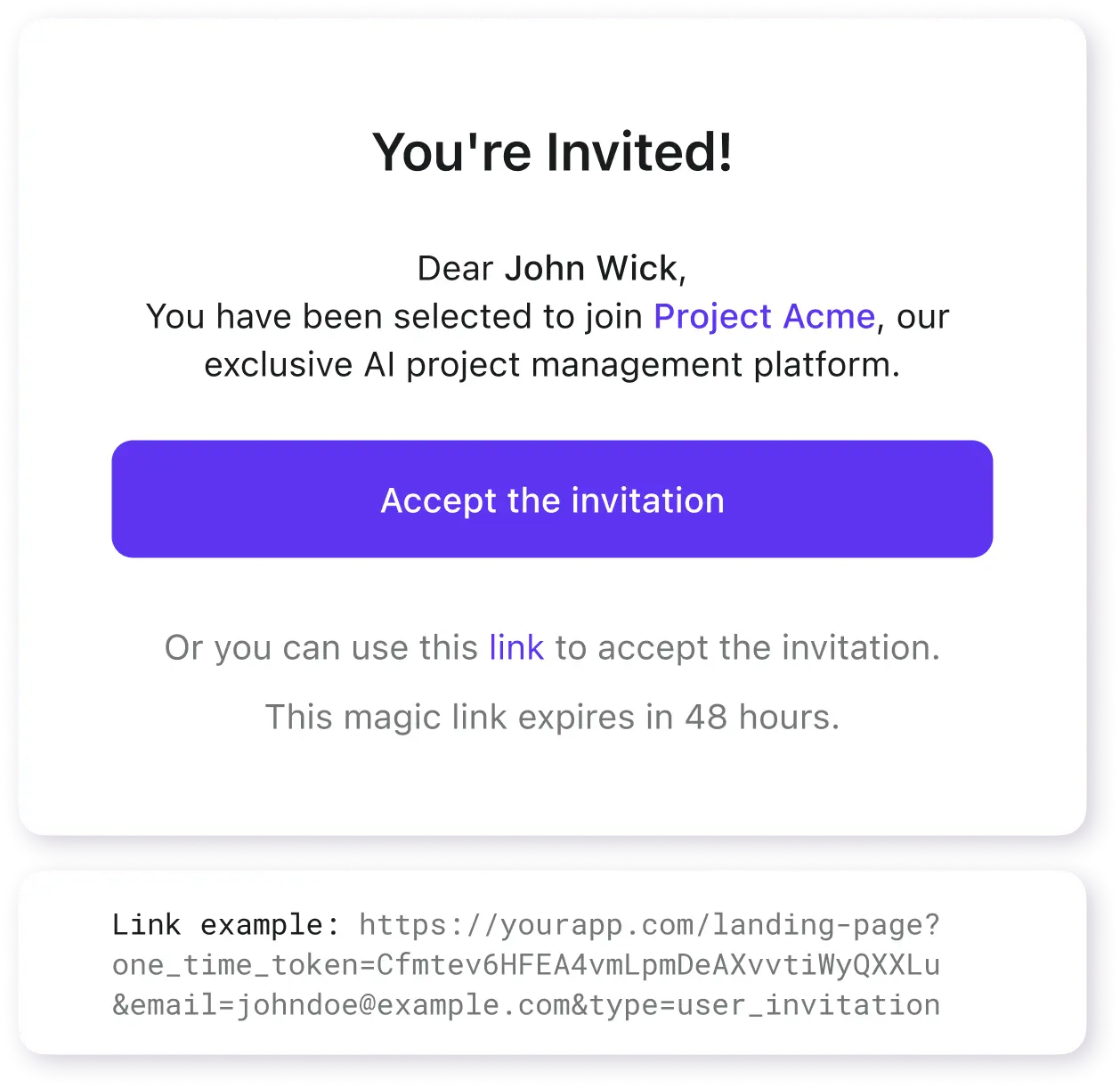
Magic link
Send unique, time-sensitive links via email or SMS. Customers join, register, or authenticate instantly. Use magic links to slash your onboarding time.
- Invitation-only sign-ups
- Organization member invitation
- Instant sign-in / sign-up
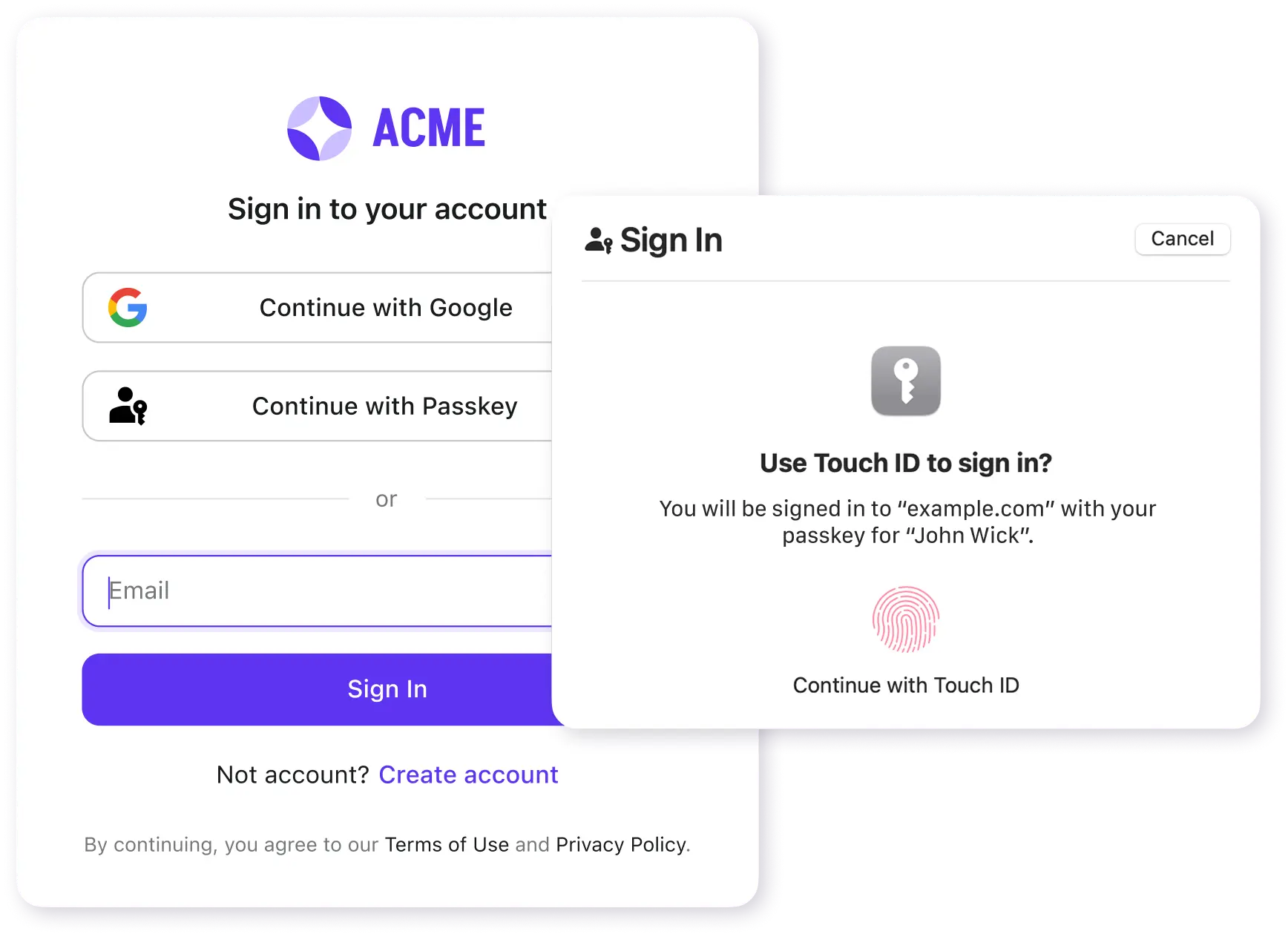
Passkey sign-in
Enable passkey sign-in that reject phishing attempts. Fast, secure access via WebAuthn standards.
- Biometrics (Face ID/Touch ID)
- Device-bound security keys
- Hardware/software authenticators
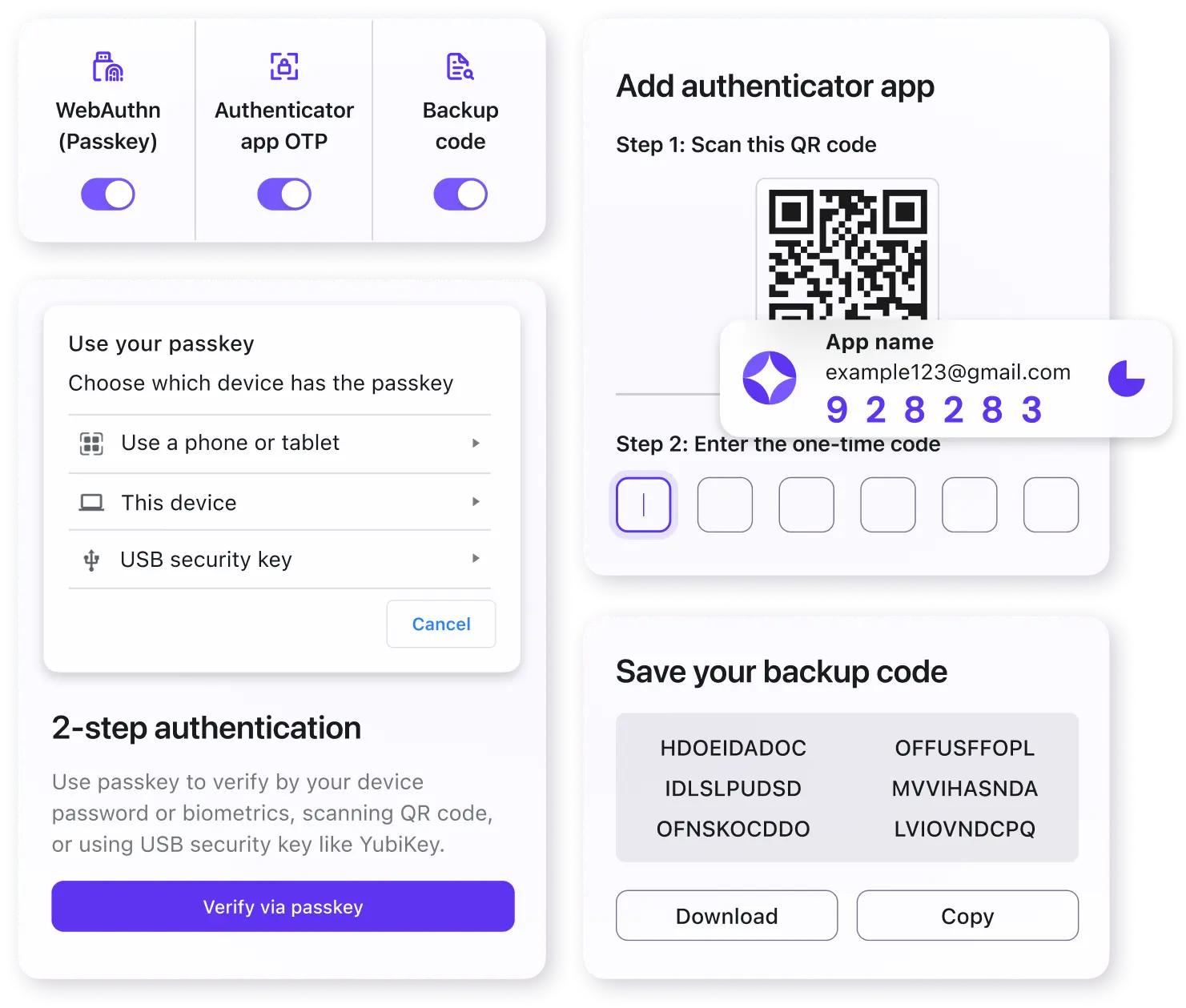
Multi-factor authentication
Multi-factor Authentication (MFA) aligns with enterprise security policies by validating that the owner of an account (or set of credentials) is actually the one trying to access the application. Nearly half of businesses use MFA to secure company data and assets.
What makes Logto the preferred choice?
Logto provides mature, out-of-the-box email and SMS passwordless sign-in solutions, designed with key principles for ease of use.
All-in-one solutions
- Ready-to-use user interface and components
- Built-in support for i18n and localization
- Configurable and API-ready
Put security first
- Expiration times and resend options
- Full compliance with OIDC standards
Flexible and customizable
- Cover over 90% sign-in experience scenarios, proudly
- Supports multiple sign-in methods for user choice
- Customizable UI for tailored user flows
Easy implementation and management
- Audit logs to track sign-in activity
- Simple 3-step, 10-minute integration
- 30+ SDK for quick setup
Frequently asked questions
How does passwordless authentication differ from email & SMS verification codes?
Is it still possible for me to use password-based sign-in if I prefer it?
Unlock more with Logto Cloud
Say goodbye to passwords and hello to hassle-free authentication with Logto's email and SMS passwordless sign-in. Give it a try now and discover a simpler and more secure way to acquire and protect your customers.