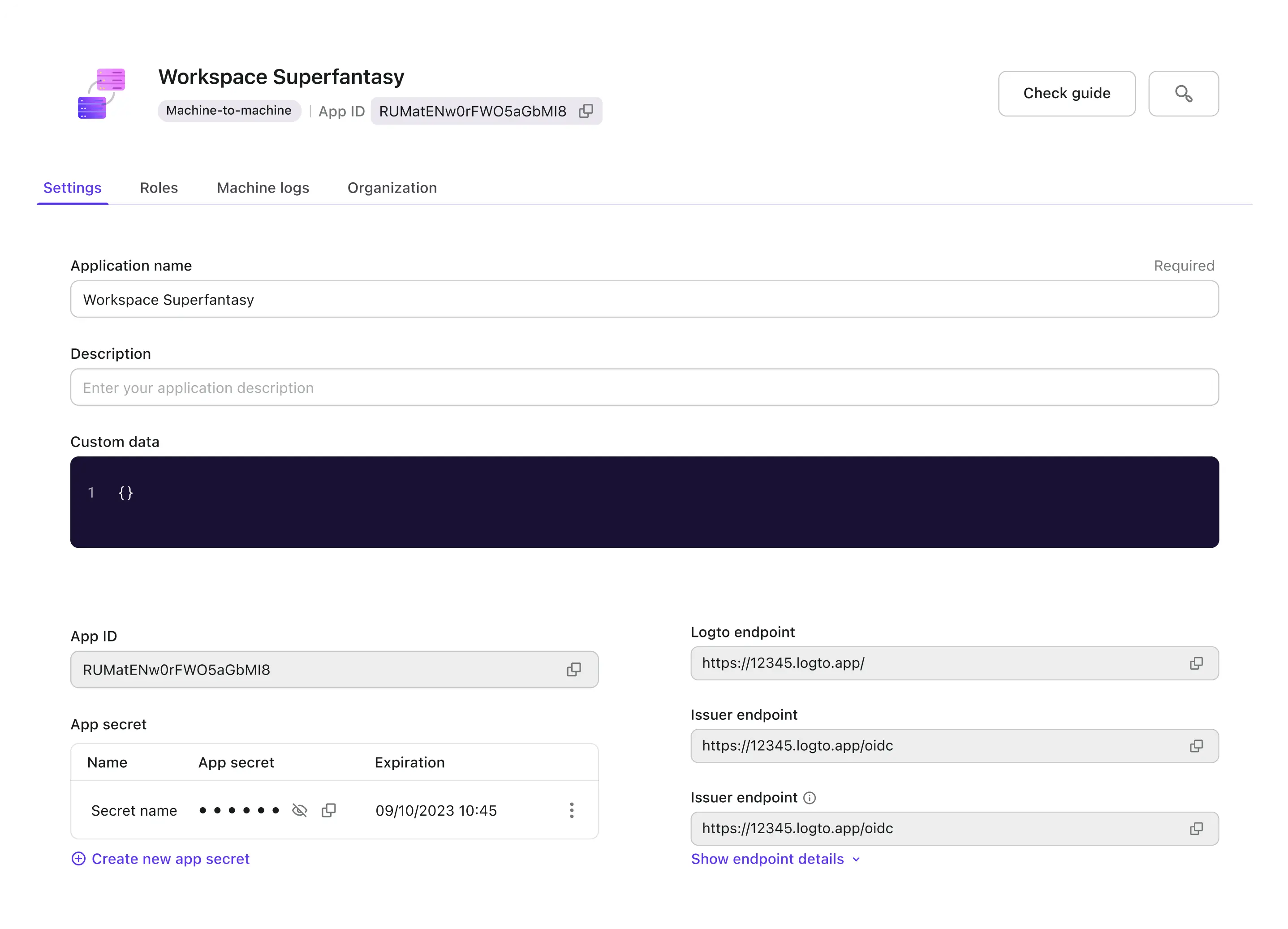
Secure APIs and services communication
Logto secures your API communications and service integrations with machine-to-machine (M2M) authentication for real-world use cases.
Secure API communication
Machine-to-machine authentication and authorization ensure that only authorized services can access your APIs with appropriate permissions, protecting sensitive data and preventing unauthorized access to your systems.
Scalable integrations
As your system grows with multiple services and microservices, M2M authentication and authorization provide a scalable way to manage service-to-service communication with proper access controls.
IoT device communication
M2M authentication and authorization provide secure and reliable communication channels between IoT devices, enabling seamless data exchange and coordinated operations across distributed IoT networks.
What you can do with Logto’s machine-to-machine?
Explore practical ways to leverage Logto’s M2M capabilities to connect trusted services, secure API access, and enable automated workflows.
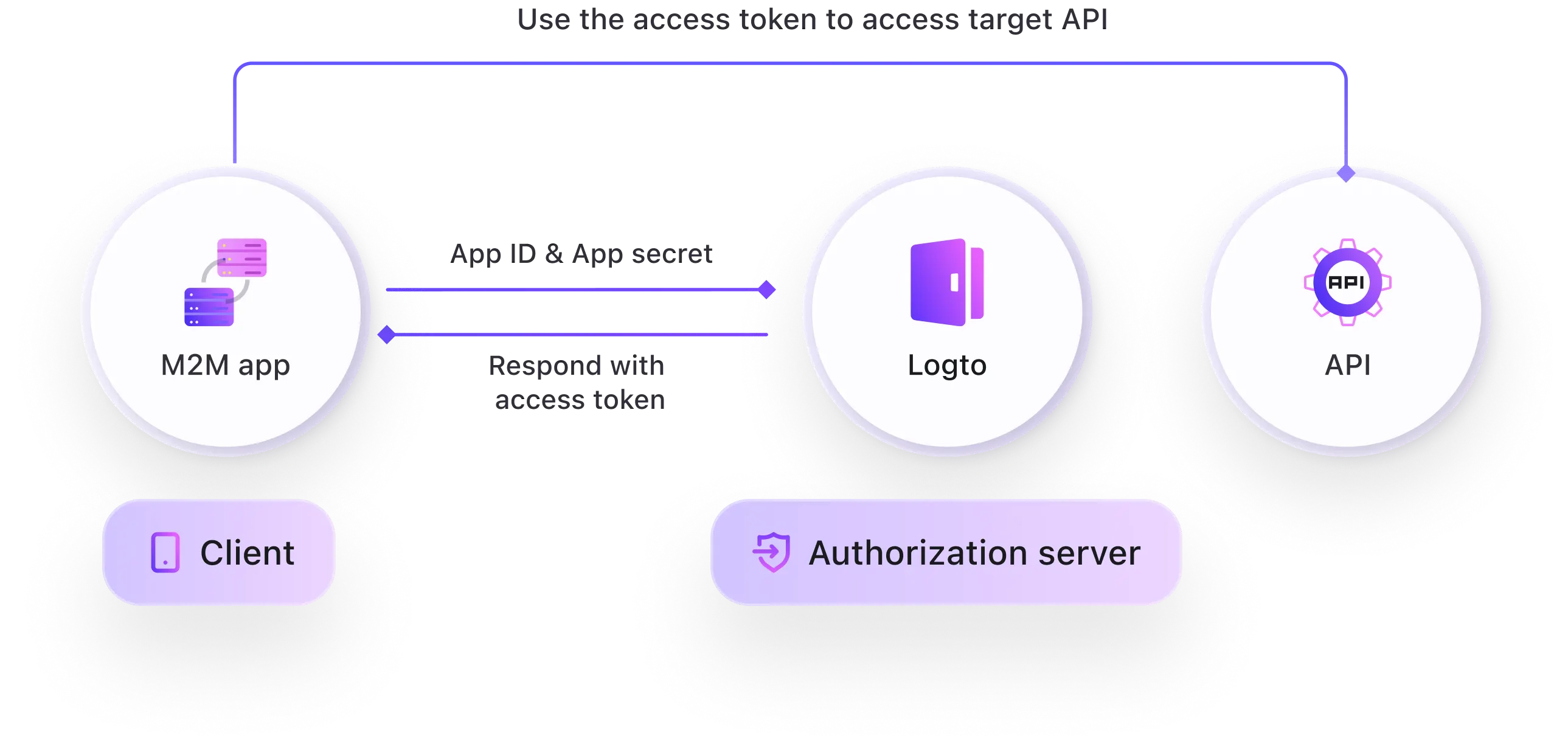
Use M2M to securely authenticate non-human apps
Non-interactive apps can securely access the target API using the M2M flow:
- App sends App ID and App Secret to Logto
- Logto verifies them
- Logto issues an access token
- App uses the token to call the API; API validates and grants access.
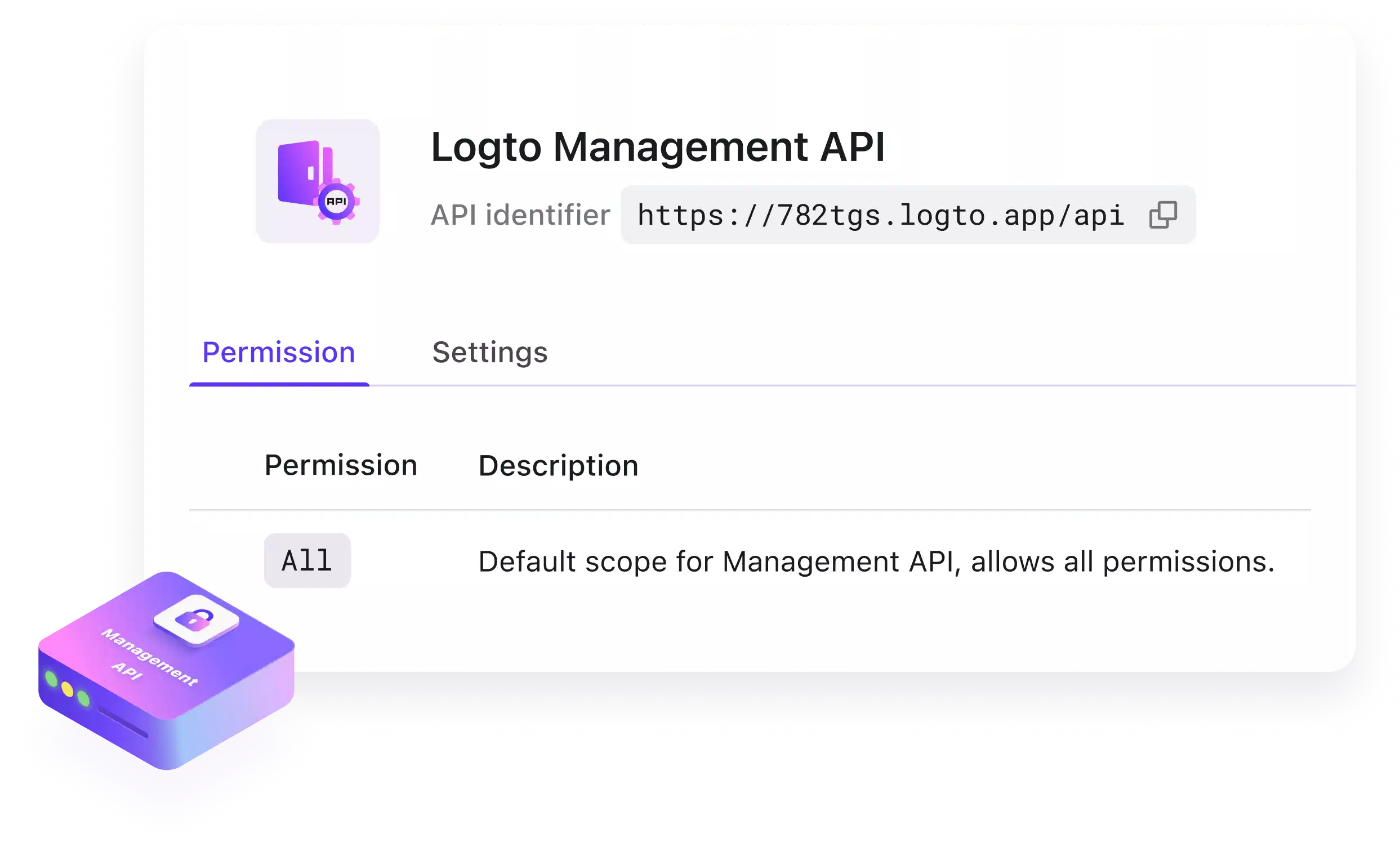
Access Logto Management API with machine-to-machine
For accessing Logto Management API, you would use M2M authentication with Client Credentials Flow for operations like,
- Automated user provisioning
- Bulk user updates
- Automated role assignments
- System monitoring and analytics
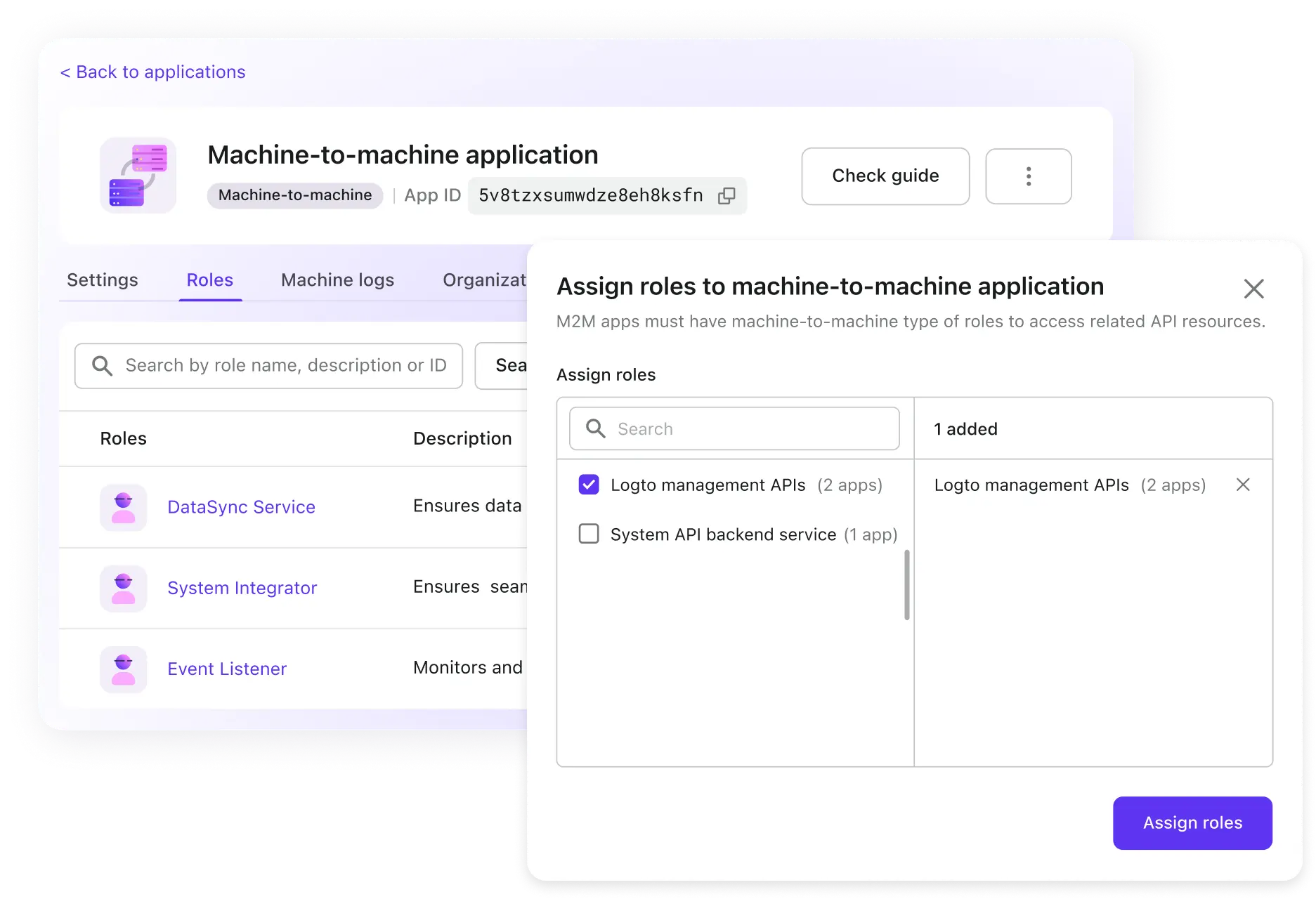
Machine-to-machine authorization
Role-based access control extends to machine-to-machine applications, ensuring devices can only access functions relevant to their assigned roles.
- Application backend service
- Command line interfaces
- Hardware and IoT devices
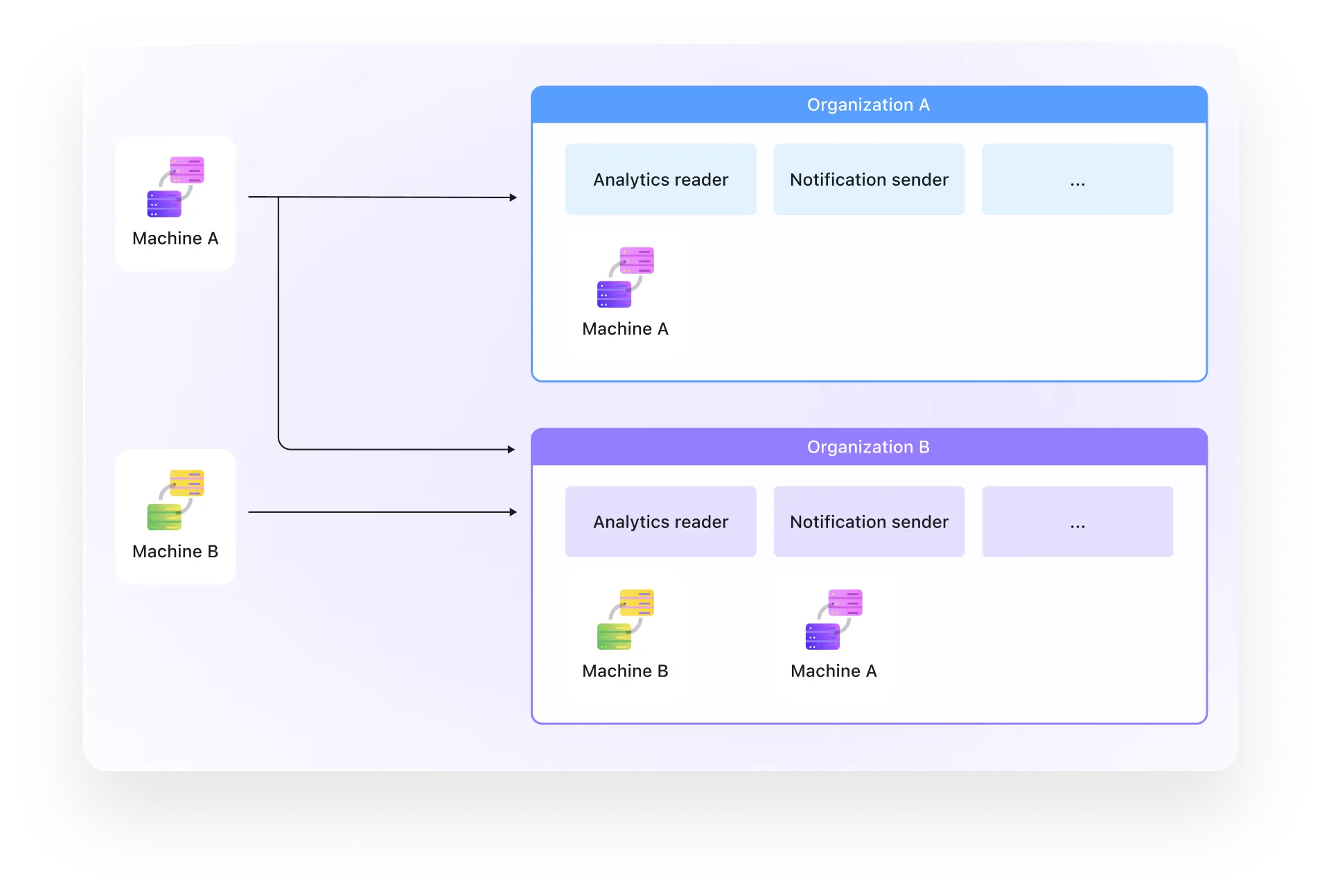
Multi-tenant SaaS
M2M supports organization-level isolation, enabling secure service-to-service communication in multi-tenant environments.
- M2M apps can be assigned to specific organizations
- Apps can have different roles per organization (e.g. Analytics reader in Org A, Notification sender in Org B)
- Organization-level isolation prevents cross-tenant access, even for backend services
Enterprise-grade M2M security for modern applications
Our machine-to-machine solution provides enterprise-grade security and access control for your service communications while maintaining developer-friendly implementation.
No human intervention required
- Fully automated authentication and authorization flows
- No user interaction needed
- Perfect for background services and APIs
Enterprise-grade security
- OAuth 2.0 and OpenID Connect compliant
- Strong cryptographic token handling with scopes
- Comprehensive audit logging and access tracking
Developer-friendly implementation
- Simple SDK integration with authorization
- Clear documentation and examples
- Multiple programming language support
Scalable and performant
- High-performance token validation and authorization
- Distributed architecture support
- Built for microservices environments
Unlock more with Logto Cloud
Secure your machine-to-machine communications and unlock the full potential of your API-driven architecture with Logto's powerful M2M authentication and authorization.