Security you don’t have to think about
Logto bakes in enterprise-grade security at every layer of your identity infrastructure—so you can protect users, reduce risk, and stay focused on building your product.
Secure your identity infrastructure
Handling authentication in-house increases exposure. A secure identity provider like Logto separates sensitive data from app logic, reducing risk and ensuring safer user authentication.
Simplified access management
Logto comes with must-have safeguards like CAPTCHA, identifier lockout, CSRF protection, and DoS defense—shielding your app from every angle.
Security best practices
Logto automatically applies modern security standards—like strong password policies, key rotation, user suspension, and OIDC back-channel logout—so you don’t have to set it up manually or worry about missing anything.
Security that adapts to you
Logto offers a wide range of customizable security features—letting you tailor protection to fit your app’s specific requirements.
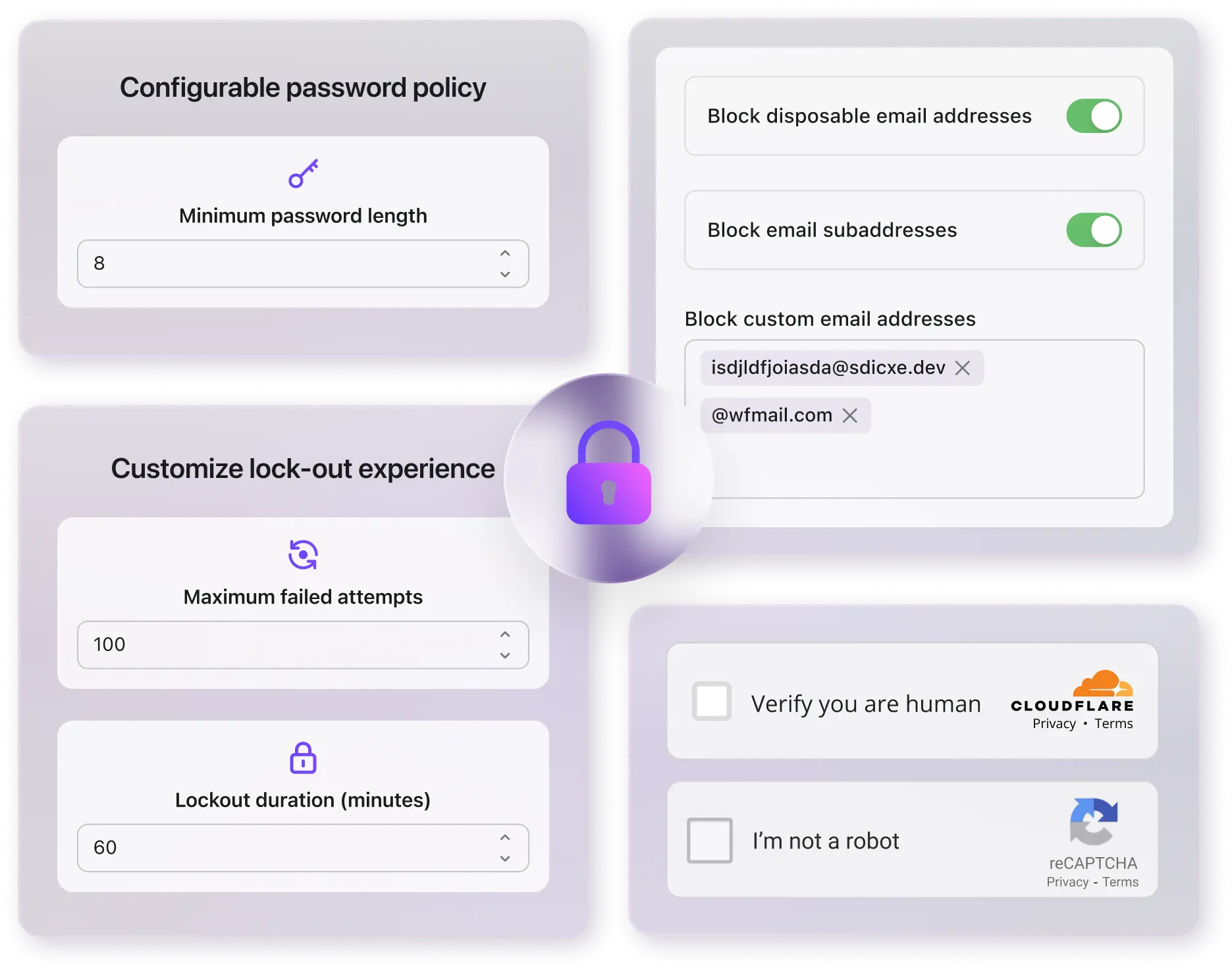
CAPTCHA
Add CAPTCHA, like Google reCAPTCHA Enterprise or Cloudflare Turnstile, to your sign-in flow to block automated bot attacks and keep malicious traffic out. Works for multiple scenarios:
- Sign in
- Sign up
- Forgot password
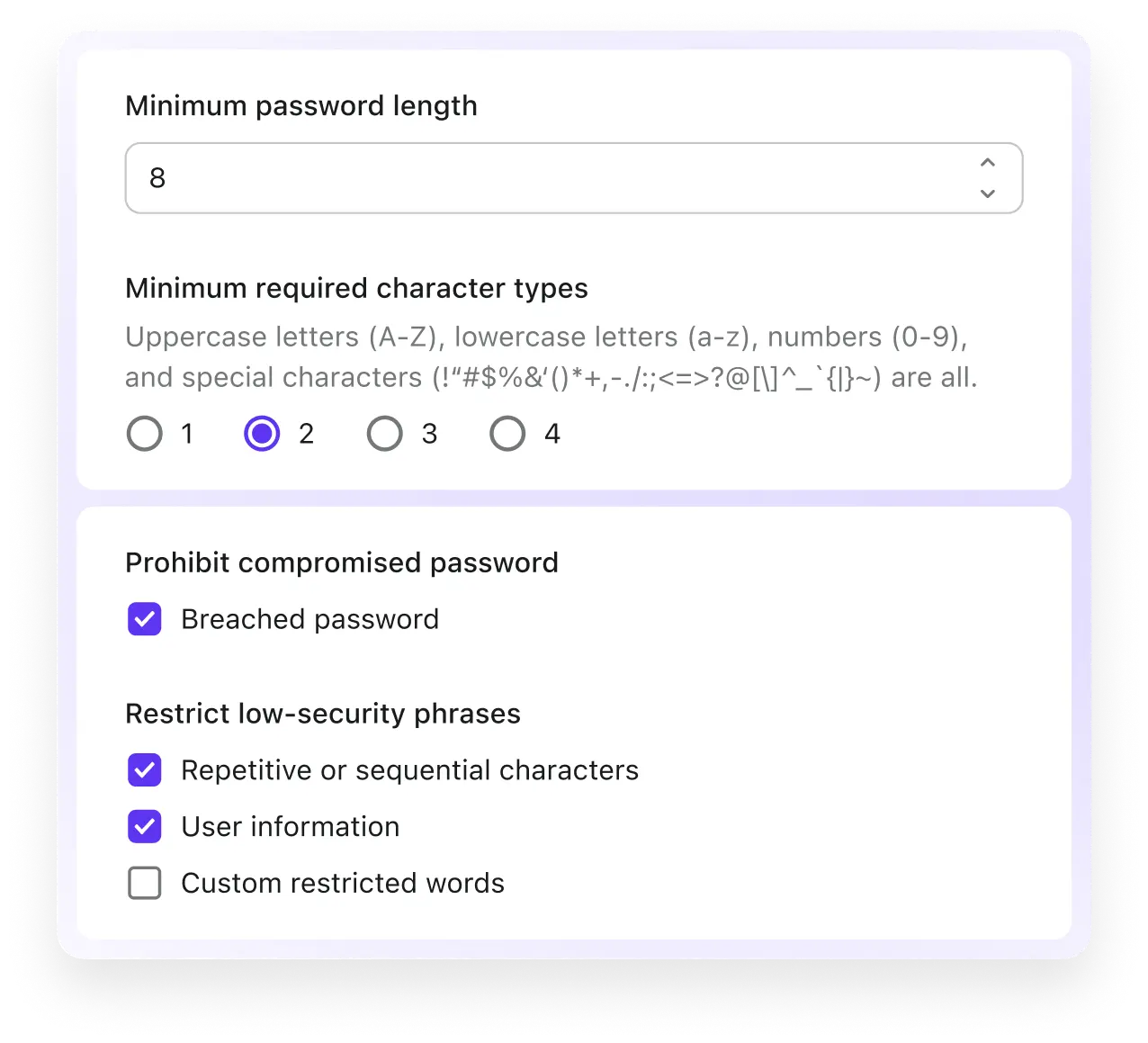
Configurable password policy
Follow NIST password guidelines and customize your password policy to match your preferred security level.
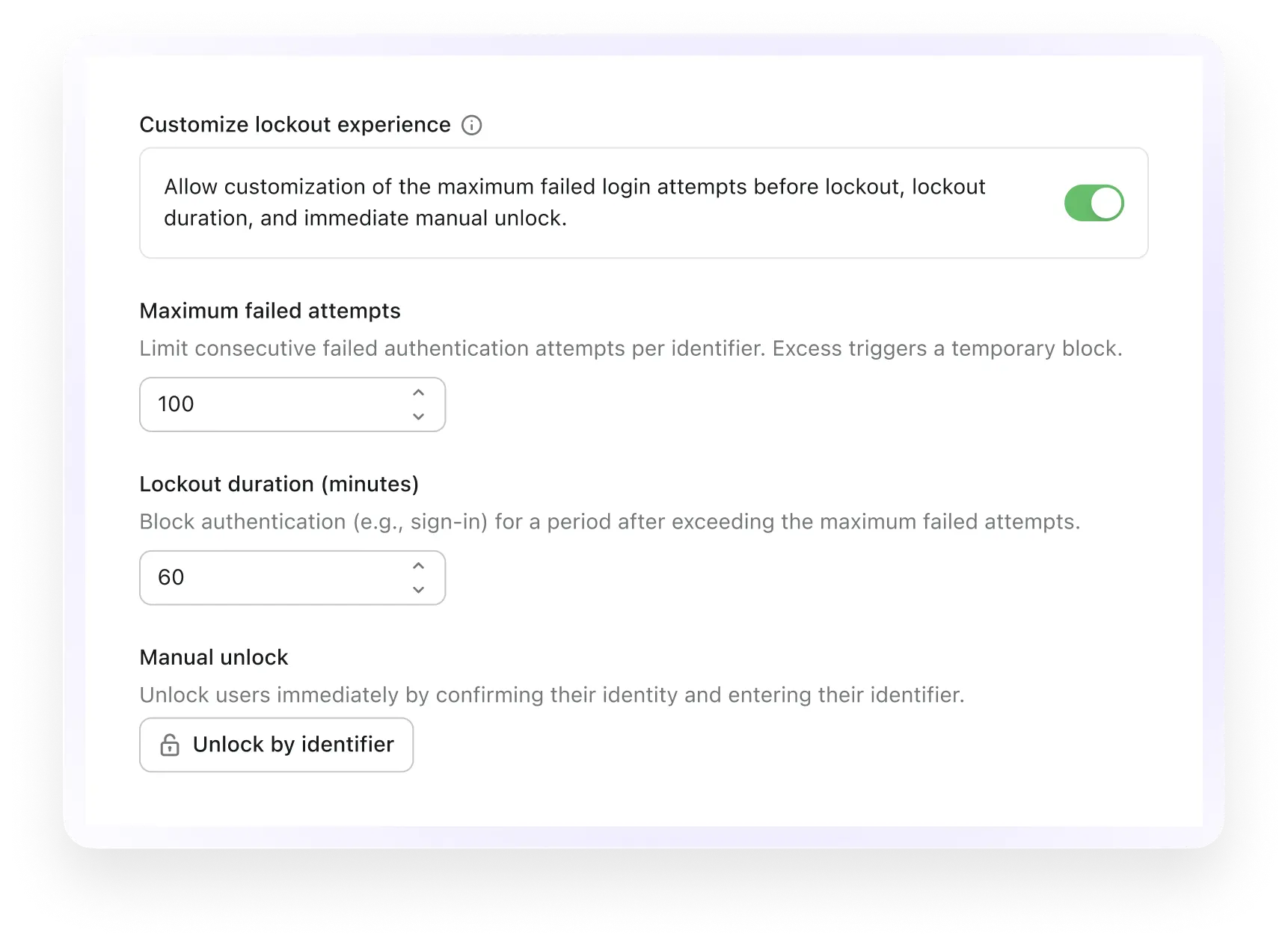
Identifier lockout
Temporarily lock an identifier after repeated failed sign-in attempts to block brute force attacks and protect user accounts.
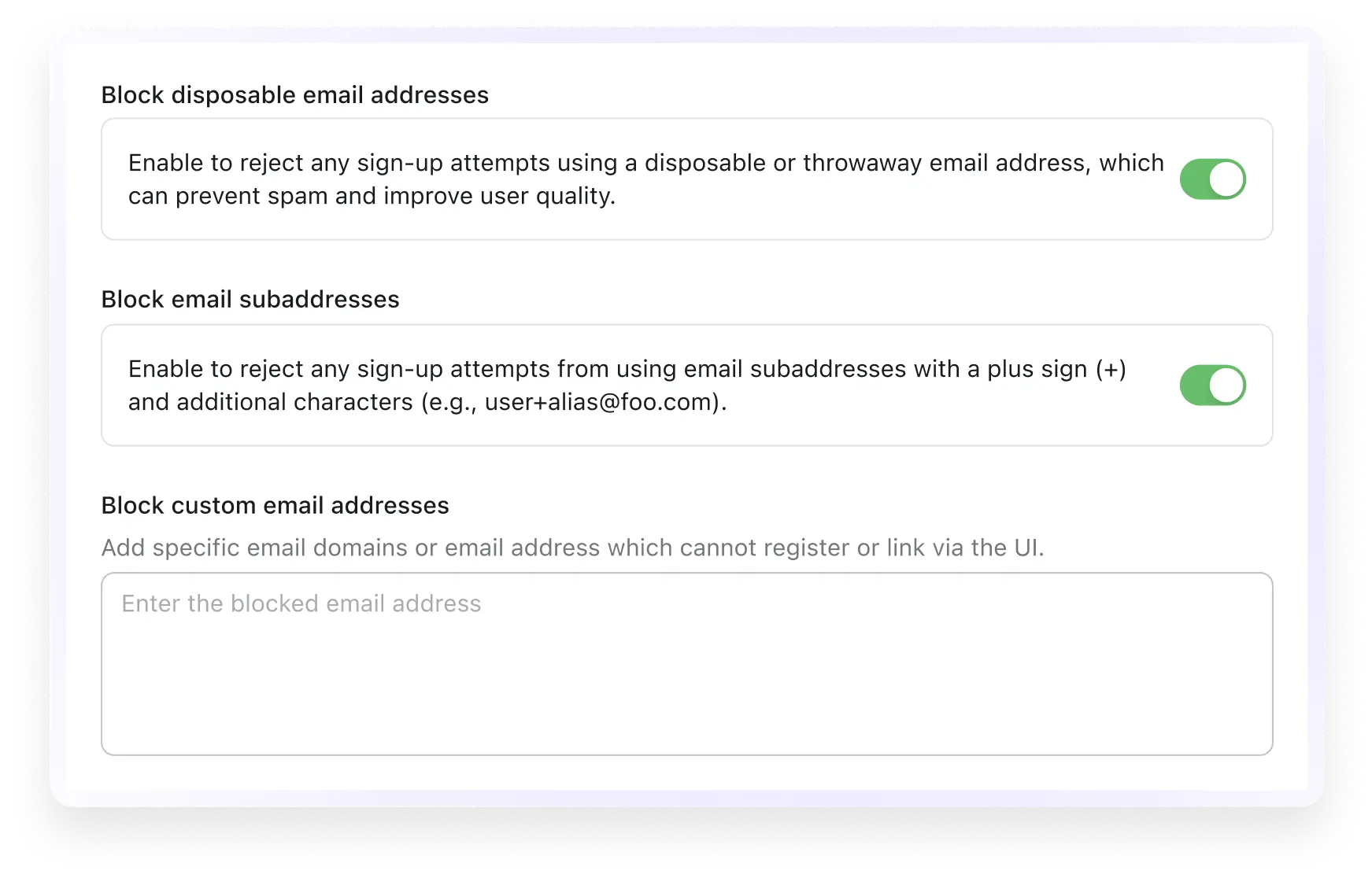
Email blocklist
Take control of your user base by blocking disposable email, subaddresses, or unwanted email domains or addresses.

Invitation-only sign up
Restrict sign-ups to invited users only with secure email magic links. Powered by Logto��’s one-time token feature, this ensures safe and controlled onboarding—perfect for waitlists or sensitive platforms.
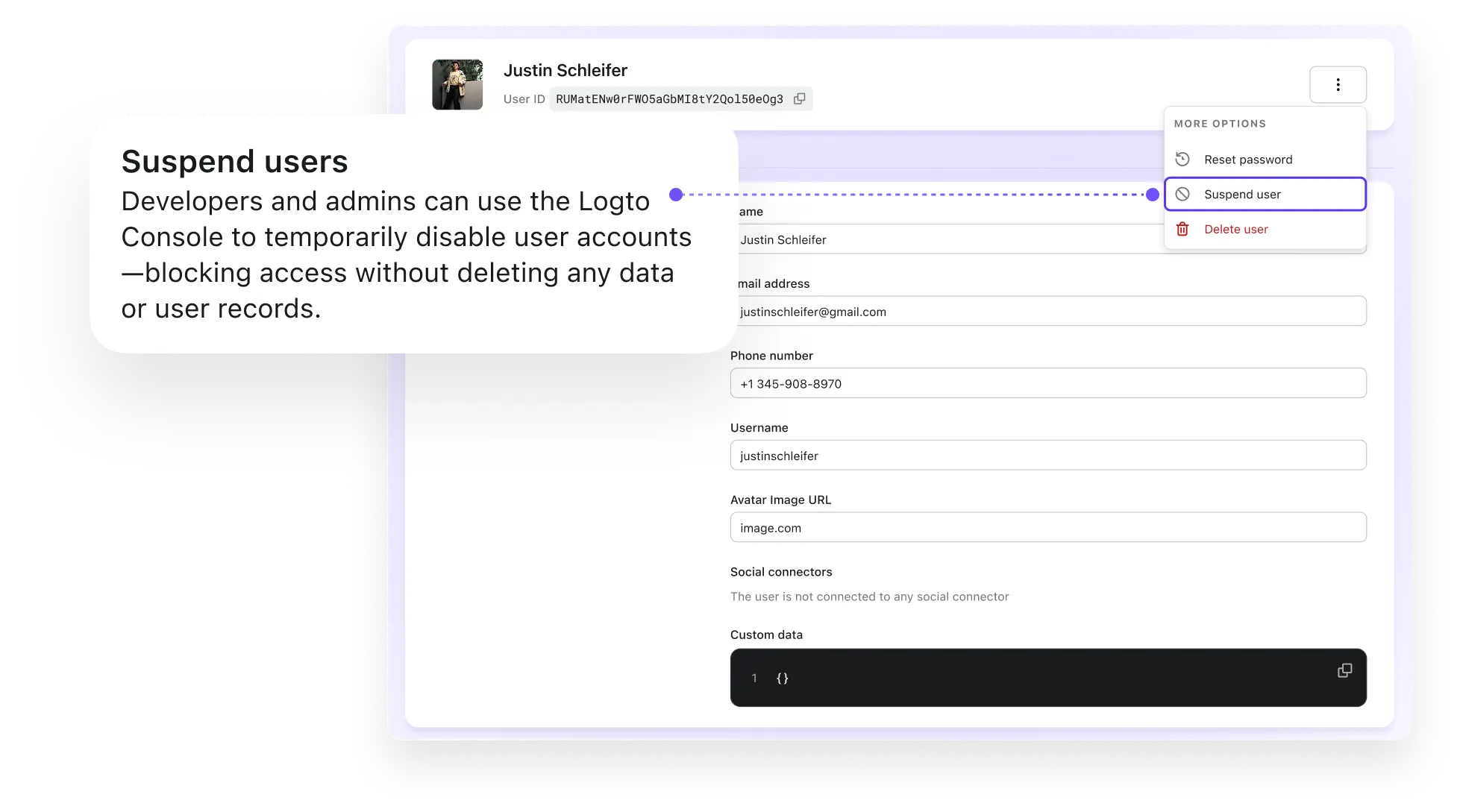
Suspend users
Temporarily disable user accounts to block access without deleting data or user records.
Core security features for all plans
Security is foundational at Logto — beyond advanced features, core protections are built in by default and available to all users, no matter the scale.
Signing key rotation
Logto secures JWTs and cookies with configurable EC or RSA keys, and makes key rotation easy through CLI, APIs, or the Console—ensuring ongoing protection and compatibility with legacy systems.
OIDC back-channel logout
Enable centralized logout to prevent session hijacking and unauthorized access. With OIDC back-channel logout, Logto ensures all connected apps sign out together when a user logs out.
CSRF protection
Protect against CSRF attacks with Logto’s built-in security measures, including OIDC state checks, PKCE, CORS enforcement, and secure cookie handling—ensuring that only trusted requests can initiate authentication flows.
DoS protection
Defend against flood and application-layer attacks with Cloudflare, Azure firewalls, rate limiting, and Logto’s scalable infrastructure—all designed to keep your identity system resilient under pressure.
Frequently asked questions
Does Logto support DDoS protection and rate limit?
Unlock more with Logto Cloud
Gain greater control over access permissions and improve security with Logto's powerful RBAC (role-based access control)