Why Secret vault powers the next generation of connected applications?
Unlock limitless possibilities for AI agents, SaaS platforms, and enterprise applications with secure third-party token storage and management.
Supercharge AI agent capabilities with secure integrations
AI agents need access to multiple third-party services to deliver automated experiences.
Enable your AI products to securely access user data from Google Suite, GitHub repositories, Slack, and more. Build intelligent automation that respects user privacy while delivering prompt-driven, context-aware experiences.
Essential foundation for modern SaaS and productivity tools
Most successful SaaS products rely on third-party integrations to deliver core business value.
Enable your SaaS or productivity tool to connect with essential third-party services that your users depend on. From CRM sync to document management, cross-platform operations are no longer optional—they're the foundation of competitive products.
Meet enterprise security standards with zero-trust principles
Enterprise clients require bulletproof security & compliance for third-party integrations.
Apply zero-trust principles through minimal privilege requests, continuous authentication, and automated token management. Balance security with user experience by refreshing tokens, while maintaining granular access controls in Logto.
Enterprise-grade solutions for secure token management
From OAuth/OIDC integrations to secure token storage, everything developers need for third-party integrations.
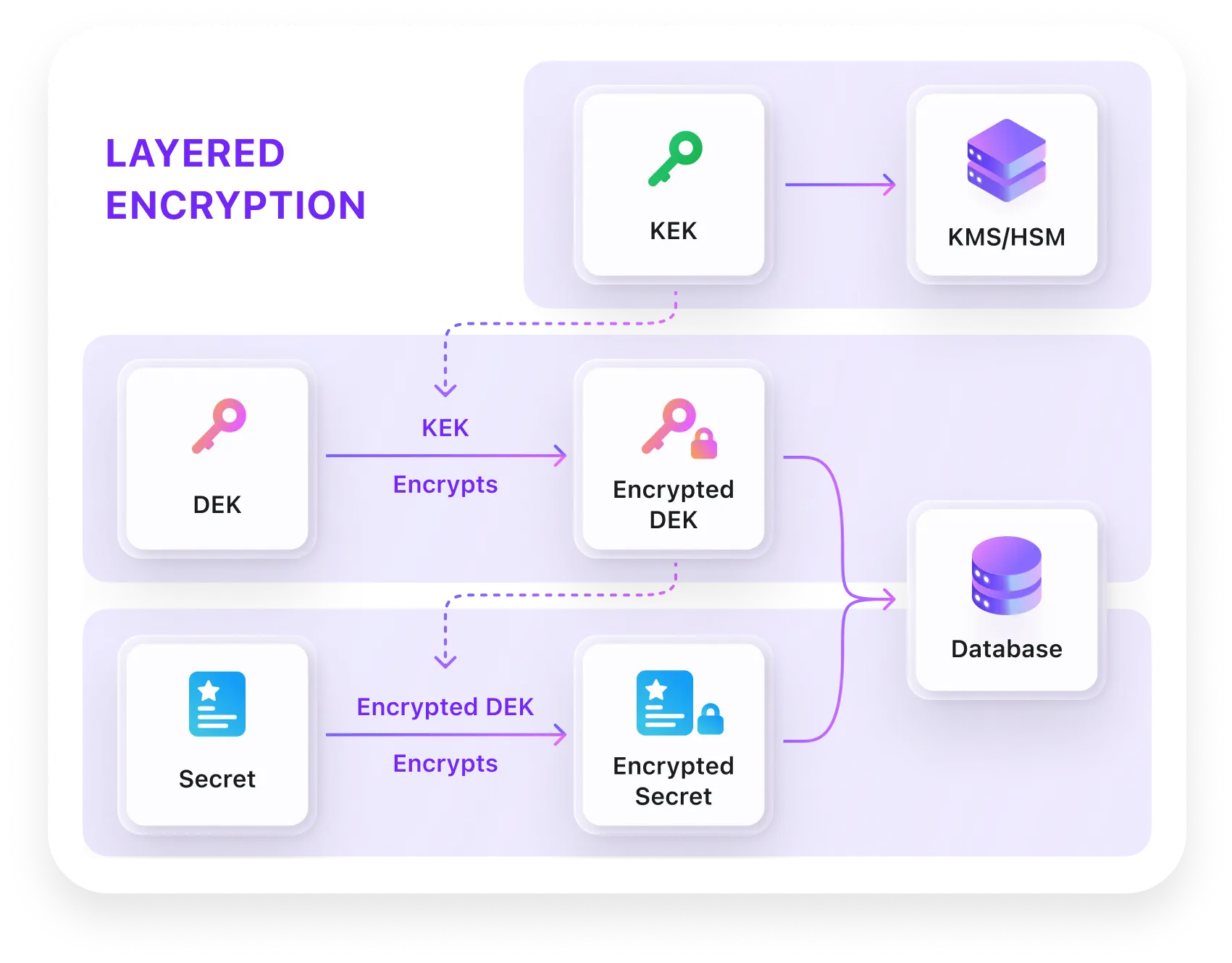
Layered encryption with unique isolation for ultimate security
Multi-layered encryption with unique isolation ensures each token is independently protected. Only end users can access their tokens, guaranteeing complete privacy and enterprise compliance.
- Store access and refresh tokens after user consent
- End-to-end encryption with individual token isolation
- Zero-knowledge design: Admins cannot view tokens
- Automated token lifecycle management and rotation
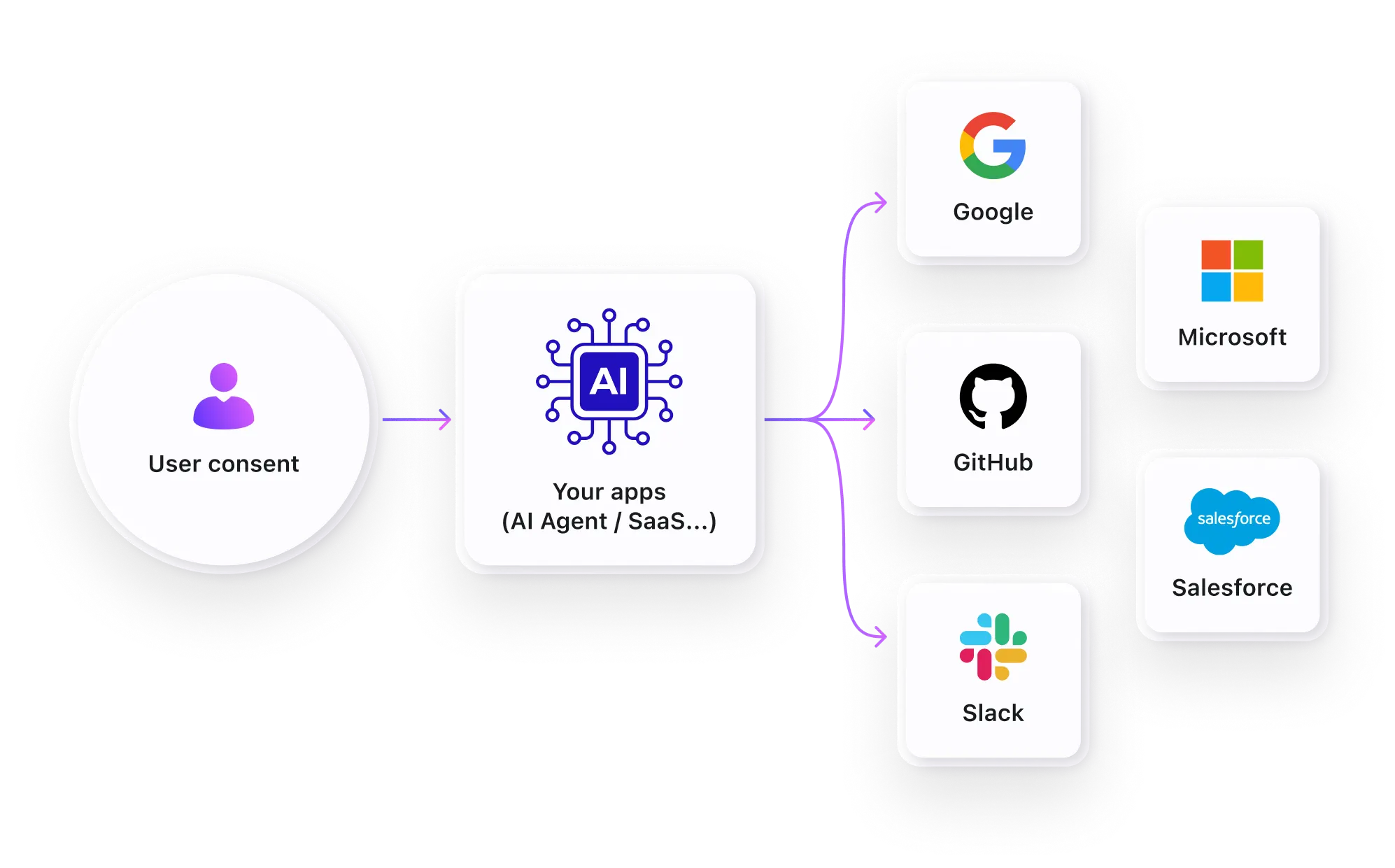
Call third-party APIs for data sync and automation
Break free from authentication limitations and unlock the full potential of third-party integrations. E.g., your AI assistant can retrieve access token with Google calendar permissions when users ask to schedule meetings.
- All business scopes support beyond user profile
- Dynamic scope escalation during user workflows
- Instant API access using securely stored user tokens
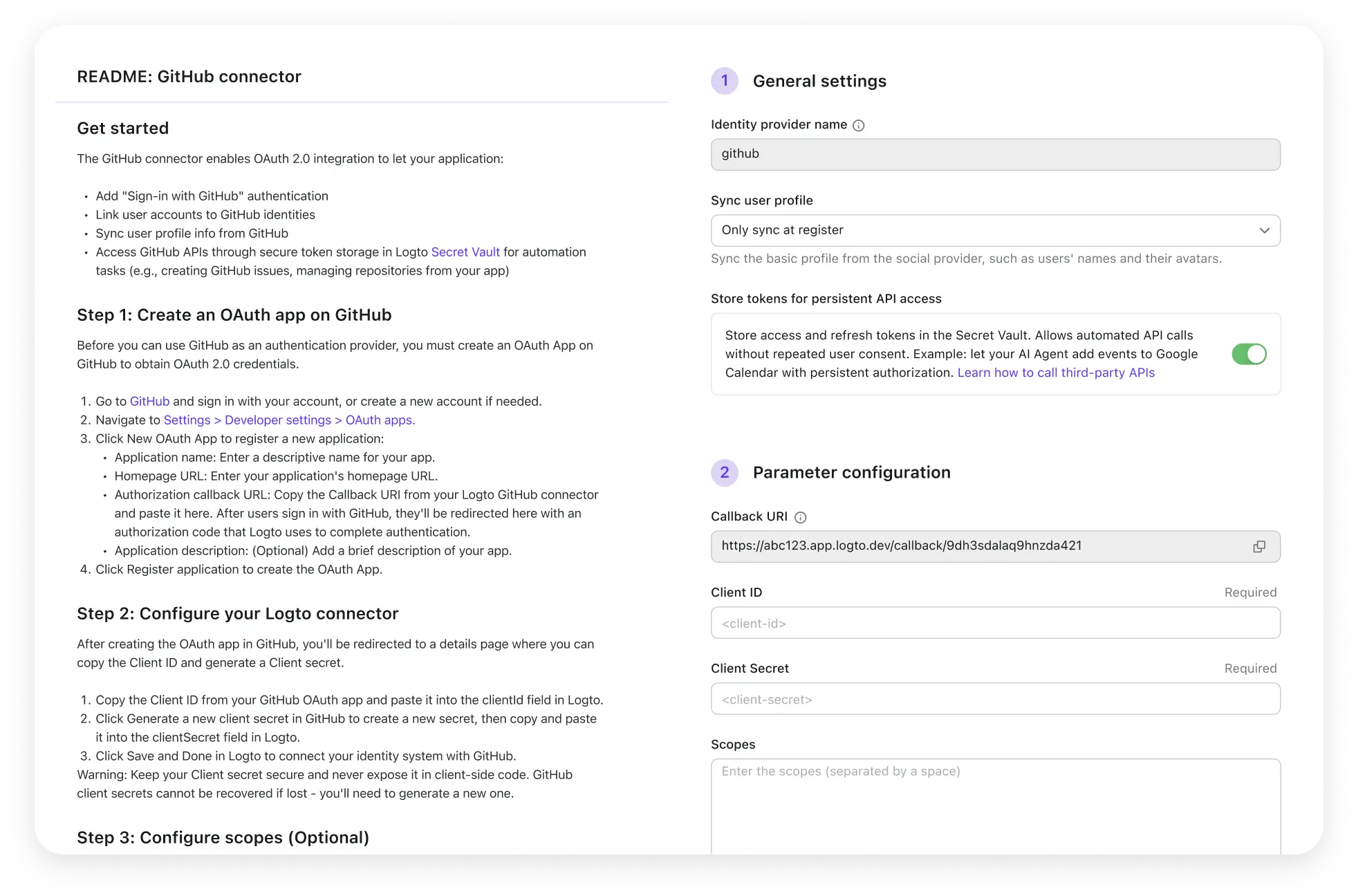
Easy OAuth / OIDC integration with step-by-step tutorials
Accelerate development with ready-to-use integrations and comprehensive developer resources. Focus on building features, not reinventing authentication infrastructure.
- Universal OIDC/OAuth support for any service
- Pre-built connectors: Google, GitHub, Facebook, etc
- Step-by-step integration guides
- Account API for programmatic token operations
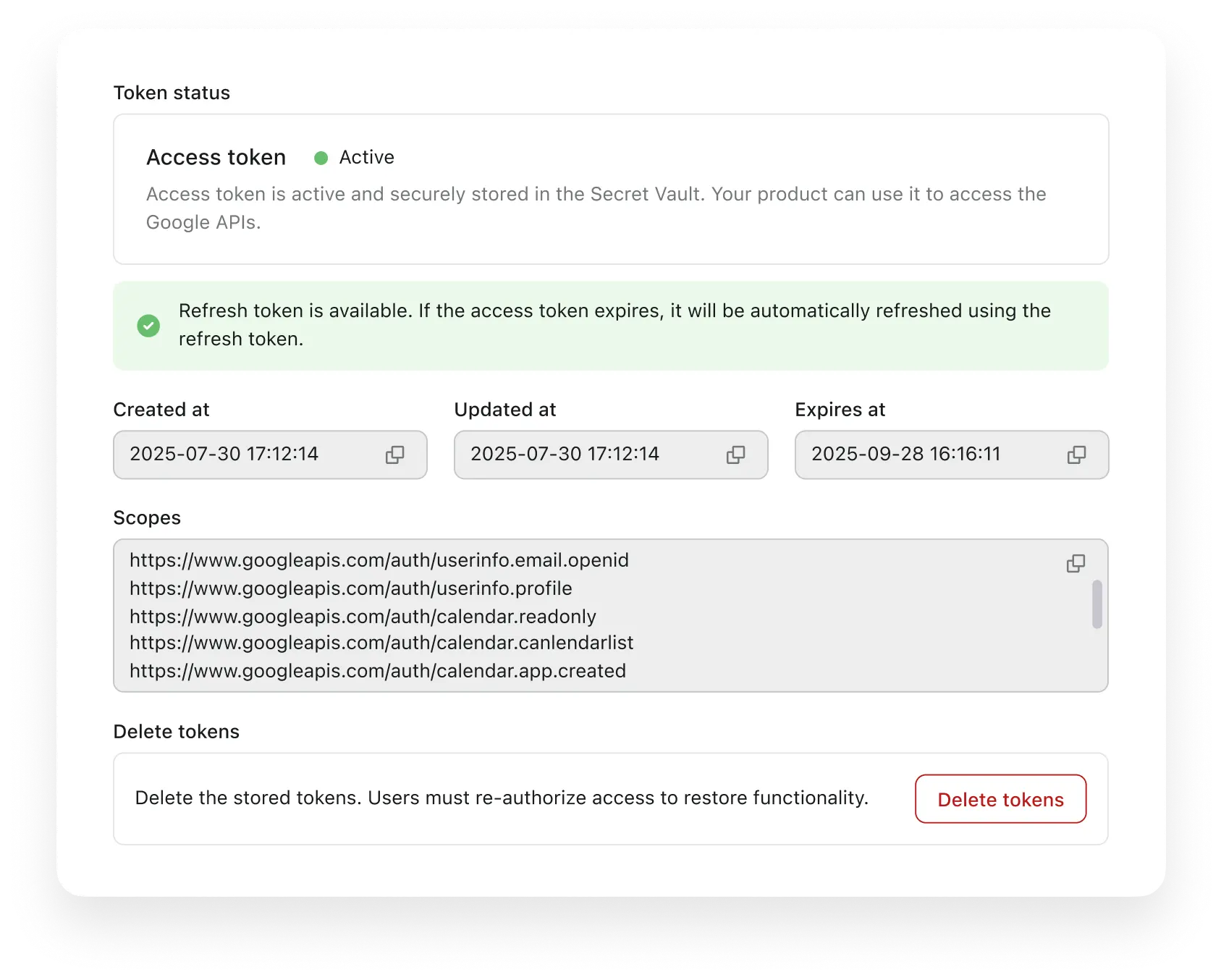
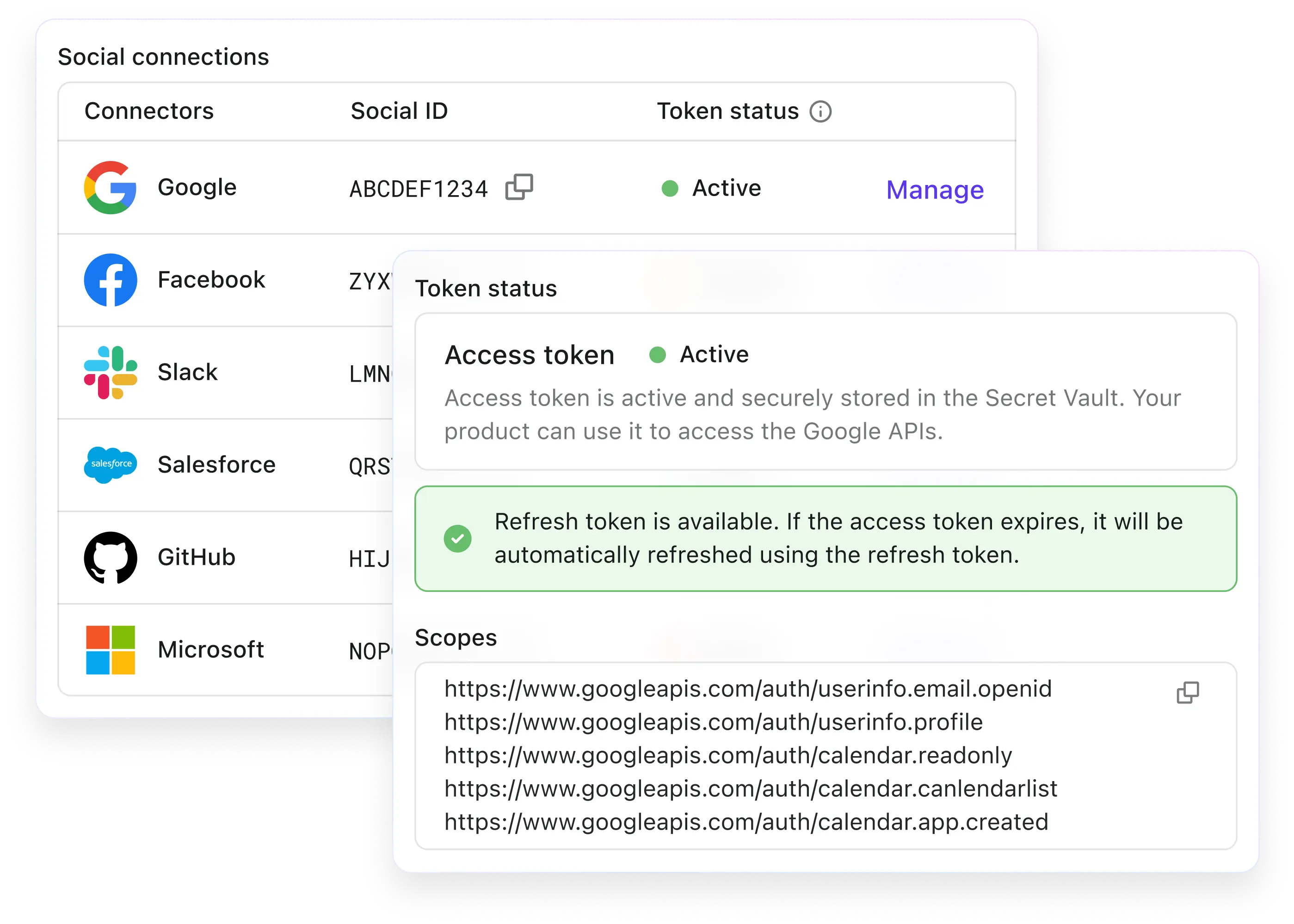
Efficient user management and token oversight
Comprehensive user management capabilities in Logto Console enable administrators to monitor, manage, and control federated token storage with complete visibility and control.
- View synced info from Social / Enterprise accounts
- Monitor token storage status and metadata
- Execute token revocation for support needs
What makes Logto Secret Vault the developer's choice?
Built for modern applications that need secure, scalable, and user-friendly third-party integrations.
Complete token lifecycle management
- Automatic token acquisition during sign-in flows, account linking, and in-app operations
- Secure storage with user-only access guarantees
- Intelligent token refresh before expiration
- Monitoring and revocation capabilities for admins
Developer-friendly integration
- RESTful Management API for all token operations
- Comprehensive SDKs for popular programming languages
- Detailed documentation with code examples
- Test environments for safe development
Frequently asked questions
Is secret vault only used for storing third-party tokens from connectors?
How does Secret Vault ensure that administrators cannot access user tokens?
Can I integrate Secret Vault with custom third-party services?
What happens if a stored token expires or is revoked?
Unlock more with Logto Cloud
Start building secure third-party integrations with Logto Secret Vault.